Method for data security transmission and key exchange
A technology for key exchange and data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
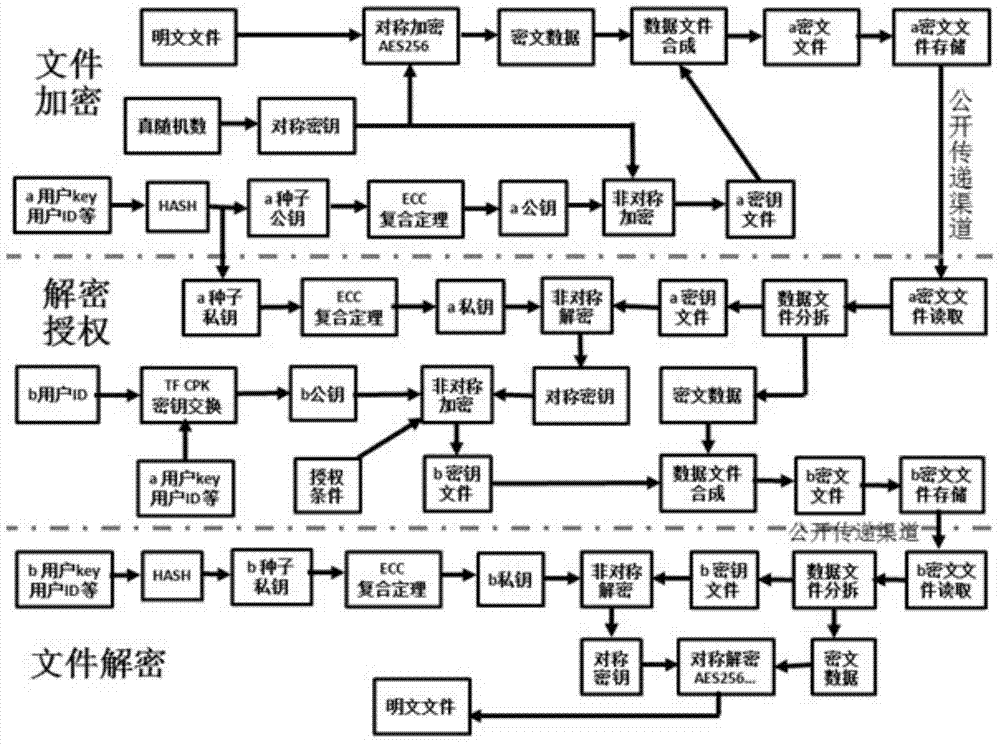
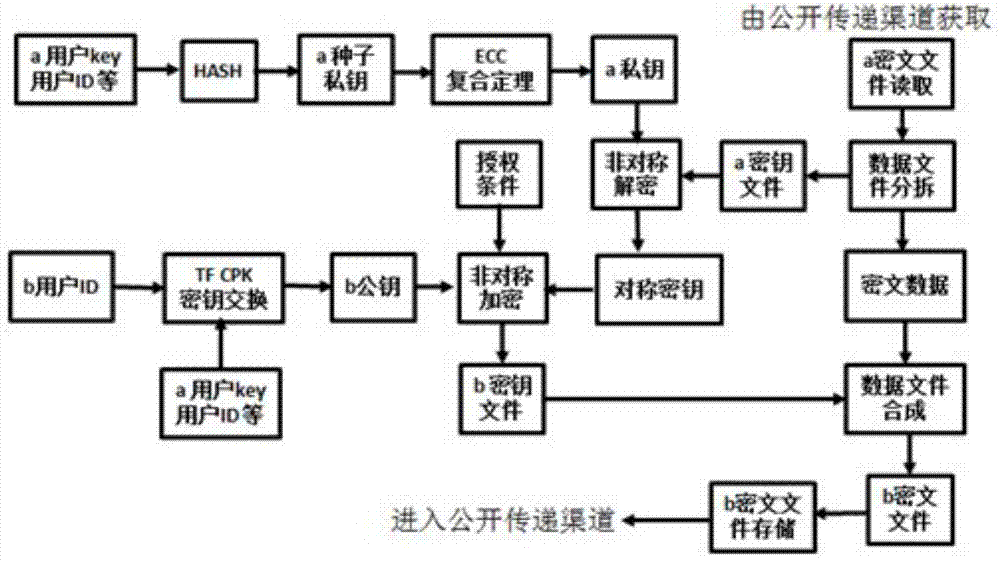
[0031] combine Figure 1 to Figure 4 Describe this embodiment mode, a method for secure data transmission and key exchange described in this embodiment mode, the implementation process of the method for secure data transmission and key exchange includes three parts: plaintext file encryption, decryption authorization, and ciphertext file decryption. The specific process is as follows:
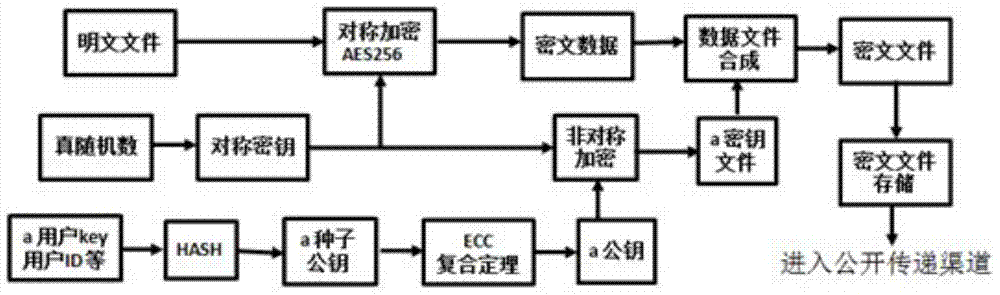
[0032] Step 1, plaintext file encryption process, combined with figure 2 Further explanation:
[0033] First of all: user a wants to encrypt a file that needs to be encrypted, first read the plaintext file, and use the hardware symmetric encryption algorithm AES256 / DES / TDES / SM1 to encrypt the read plaintext file, the encrypted file called ciphertext data. Symmetric encryption ciphers are generated by a true random number generator.
[0034] Secondly, in order to preserve and securely transmit the symmetric password, use the a user public key to encrypt the symmetric encrypted password with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com