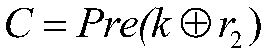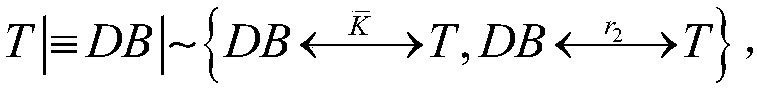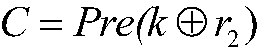Lightweight class RFID safety certification method based on Present algorithm
A security certification and lightweight technology, applied in the field of RFID system information security, can solve problems such as desynchronization attacks, achieve the effect of fewer interaction rounds, improve privacy and security attributes, and improve trustworthiness and real-time performance
Active Publication Date: 2017-09-15
BEIJING UNIV OF POSTS & TELECOMM +1
View PDF6 Cites 12 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In 2007, Chien HY worked on ultra-lightweight SASI authentication protocol (H Y Chien. SASI: A new ultralightweight RFID authentication protocol providing strong authentication and strong integrity [J]. IEEE Transactions on Dependable and Secure Computing, 2007, 4(9): 337-340 ) only uses a limited number of ultra-lightweight algorithms such as XOR (exclusive OR) and cyclic shift to realize the challenge-response, and establishes two key storage units in the background database to improve the key recovery ability, but due to the ROT function The algebraic properties of SASI are proven to be susceptible to bit tampering (Dimitriou,T.(2005).ALightweight RFID Protocol to protect against Traceability and Cloning attacks[C] / / Proceedings of First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SecureComm 2005), Athens, Greece, ISBN: 0769523692) Desynchronization Attacks
The protocol designed by Peris Lopez relies entirely on the reader PRNG (pseudo-random number generator) to provide freshness, which saves the computational overhead of tags, but the protocol is also vulnerable to desynchronization attacks (LiT Wang. Security analysis of two ultra-lightweight RFID authenticationprotocols[C] / / Proceedings of the IFIP TC-11 22nd International Information Security Conference IFIP SEC 2007. South Africa: 2007: 109-120) and algebraic attacks (GidasAvoine, Xavier Carpent. Strong Authentication and Strong Integrity (SASI) Is Not That Strong [C] / / The 6th International Workshop.RFIDSec 2010.Turkey: Istanbul, 2010, 50-64)
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a lightweight class RFID safety certification method based on a Present algorithm. The lightweight class RFID safety certification method based on a Present algorithm comprises steps of realizing identity mutual certification between a label and a database through sharing an old cipher key and new cipher key and secretes information between the back end database and the label, adopting a two-way random number as a fresh quantity during a protocol execution process and performing encryption calculation, wherein certification information of a label end on the database is encrypted by producing the random number from a database end and the certification information of database end on the label is encrypted by the random number generated by the label end, and executing a Present encryption algorithm to verify identities of two parties in each verification process. The lightweight class RFID safety certification method based on the Present algorithm has characteristics of safety and privacy protection, can better resist various attacks coming from the outside of the RFID system, can protect content privacy, position privacy and front and back safety and resists replay attacks, eavesdropping attacks, etc.
Description
A Lightweight RFID Security Authentication Method Based on Present Algorithm technical field The invention relates to a lightweight RFID security authentication method based on a Present algorithm, and belongs to the technical field of RFID system information security. Background technique RFID (Radio frequency identification) authentication protocol is an effective means to solve the security and privacy issues of radio frequency identification systems, but due to the limitations of low-cost RFID systems in terms of computing power and storage space, it is difficult to implement complex cryptographic algorithms and large-capacity Therefore, many existing RFID authentication protocols and solutions cannot fully satisfy the privacy and security attributes of wireless radio frequency systems. The lightweight RFID protocol proposed earlier completely relies on the randomness and unidirectionality of the Hash (hash) function to realize identity authentication and key update, s...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L9/32H04L9/08H04L9/00
CPCH04L9/002H04L9/0869H04L9/3273H04L2209/805
Inventor 高欣吕圣启张昊李新鹏闫博曹良晶刘蒙贾庆轩彭岳星
Owner BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com