Localized differential privacy protection frequent item set mining method based on frequent pattern tree
A technology of frequent itemset mining and frequent pattern tree, applied in digital data protection, special data processing applications, instruments, etc., can solve problems such as reduced practicability of the method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
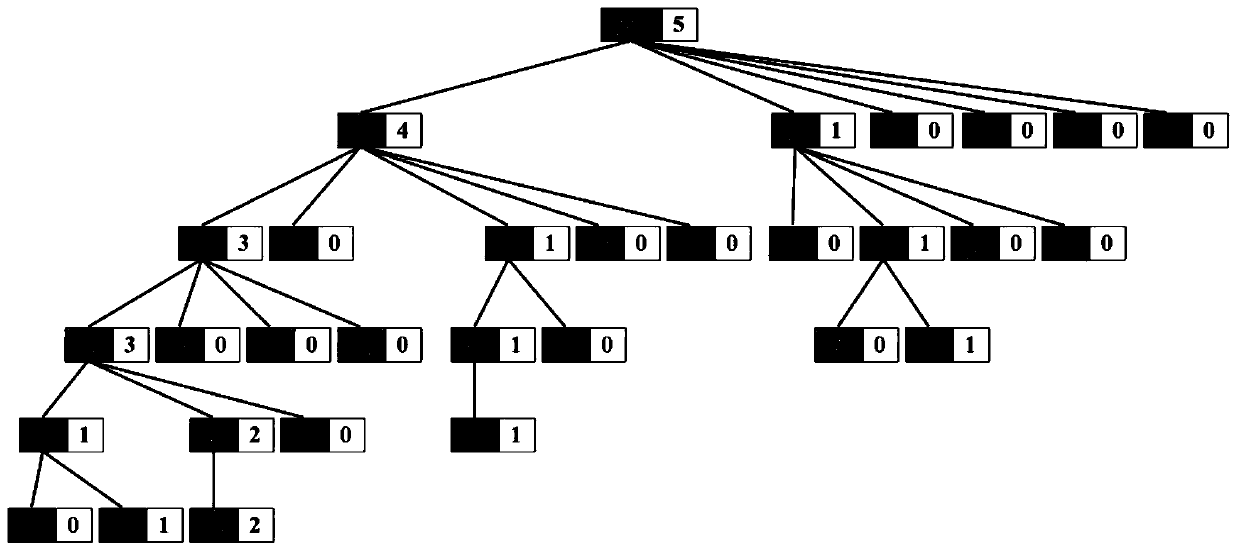
[0095] Such as figure 1 As shown, in this embodiment, a localized differential privacy-protected frequent itemset mining method based on frequent pattern trees is applied to an untrustworthy third-party data aggregator A, n users U, and privacy records V. In the scenario, the i-th user u i The privacy record of v i ,and I represents the set of known privacy items, denoted as I={x 1 ,x 2 ,...,x d ,...,x D}, x d Indicates the dth private item, 1≤i≤n, 1≤d≤D, D is the total number of private data; the frequent itemset mining method includes the following steps:
[0096] S1. Initialization phase:
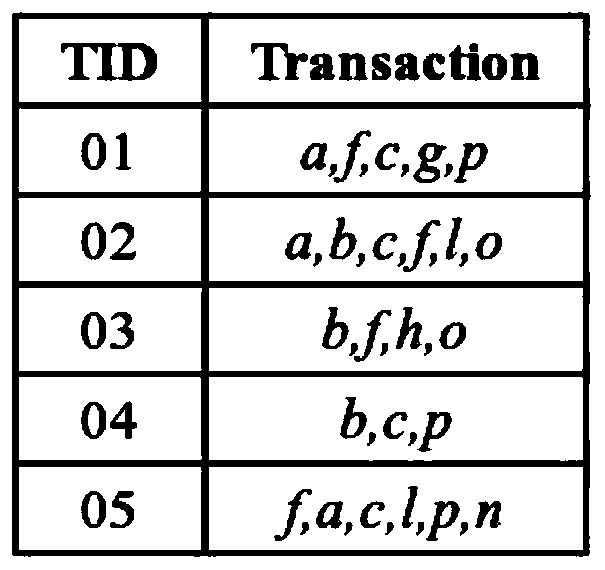
[0097] Assuming that the frequent itemset mining method is applied to a shopping mall to mine the collection of frequently purchased commodities by users, and the user's transaction records are private and unknown to the mall; given the support count threshold σ, the frequent itemsets of n user privacy transaction records Mining, you will get all the commodity sets with occurre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com