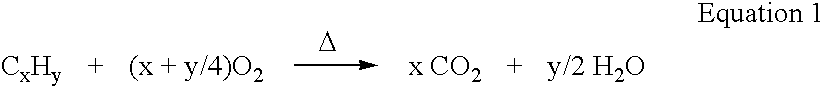Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
486results about How to "Environment safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
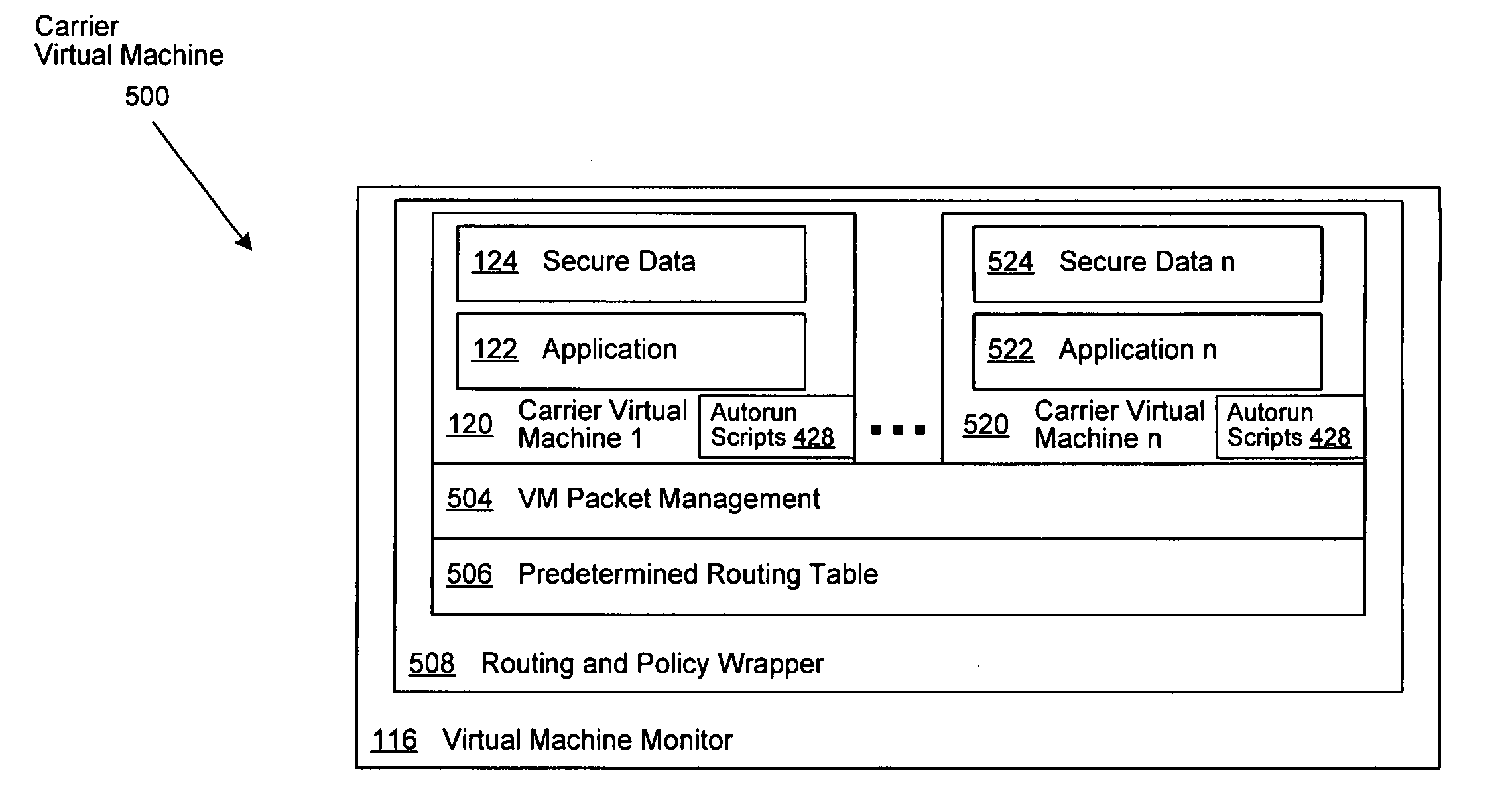
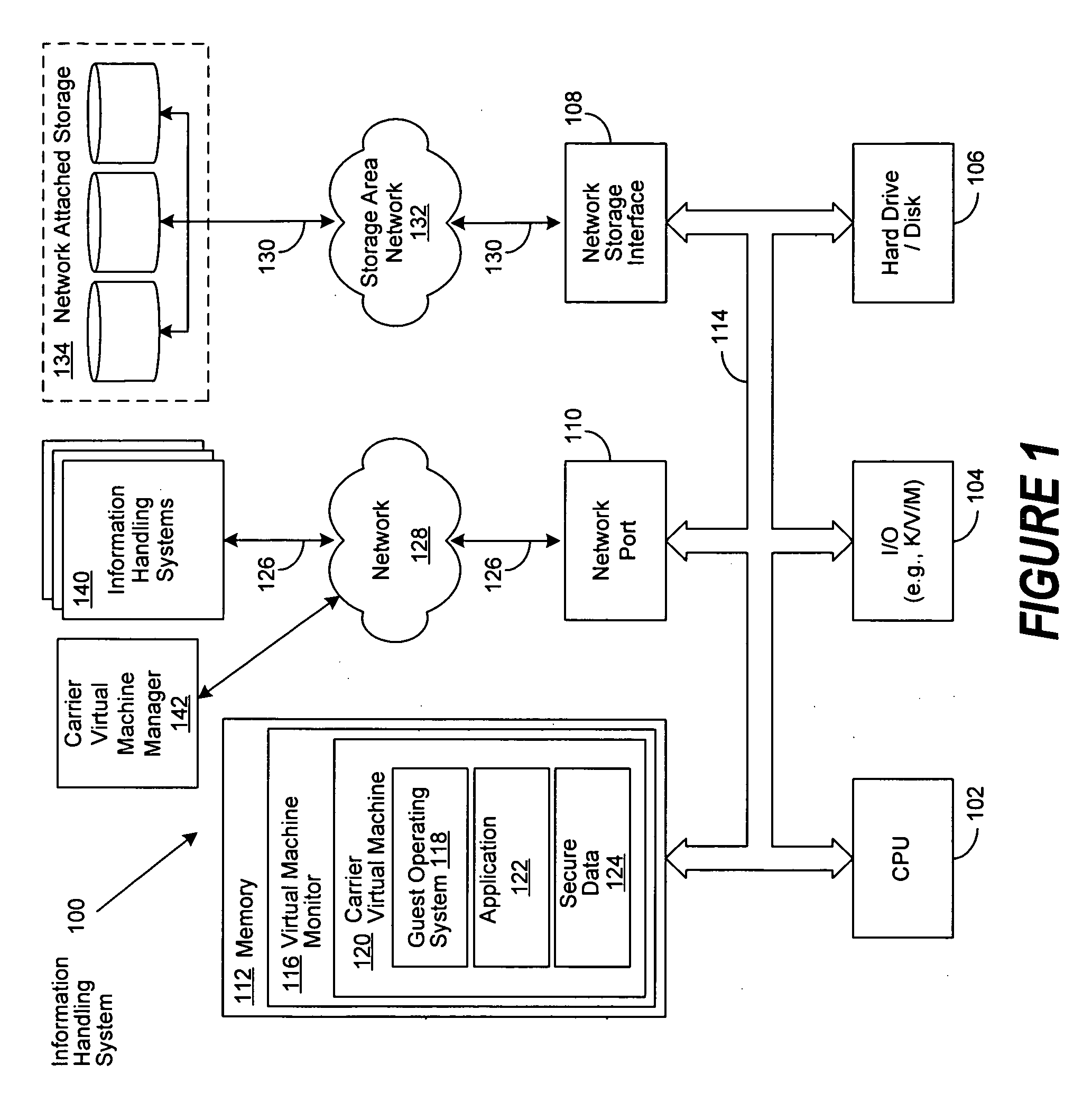
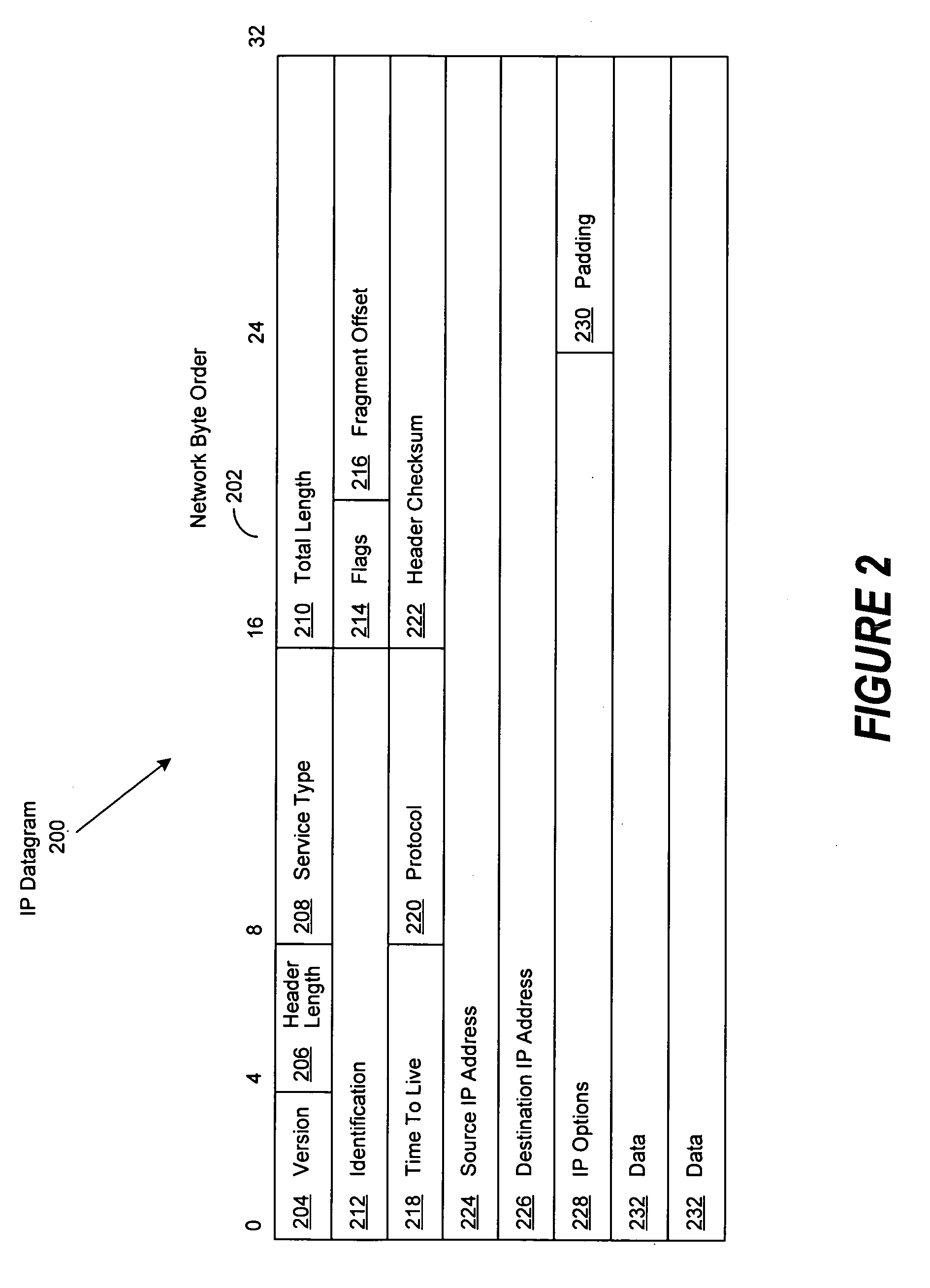
Virtual machine based network carriers
InactiveUS20070079307A1Environment safetyTransmissionSoftware simulation/interpretation/emulationData packData set
A system and method is disclosed for the secure transfer of data by carrier virtual machines between participating physical hosts through a virtual network (VNET) implemented on one or more internal and / or external networks. The method of the invention can provide additional security controls, comprising parameters that may include, but are not limited to, time-to-live (TTL), access control lists (ACLs), usage policies, directory roles, etc. Additionally, access to one or more of a plurality of carrier virtual machine payloads by security groups, individual access, subdivided individual access, and MIME-like subdivision of a VM-encapsulated payload may be controlled, thereby providing the carrier VM the ability to carry many secured payloads. In addition, VM packets, a group of packets, a single VM, or subpackets within a VM between network endpoints, or at a predetermined intermediary network point, may be quarantined to realize further security. Individual or combinations of these functionalities on carrier virtual machines, and by extension, application and / or one or more sets of secure data may be implemented.
Owner:DELL PROD LP
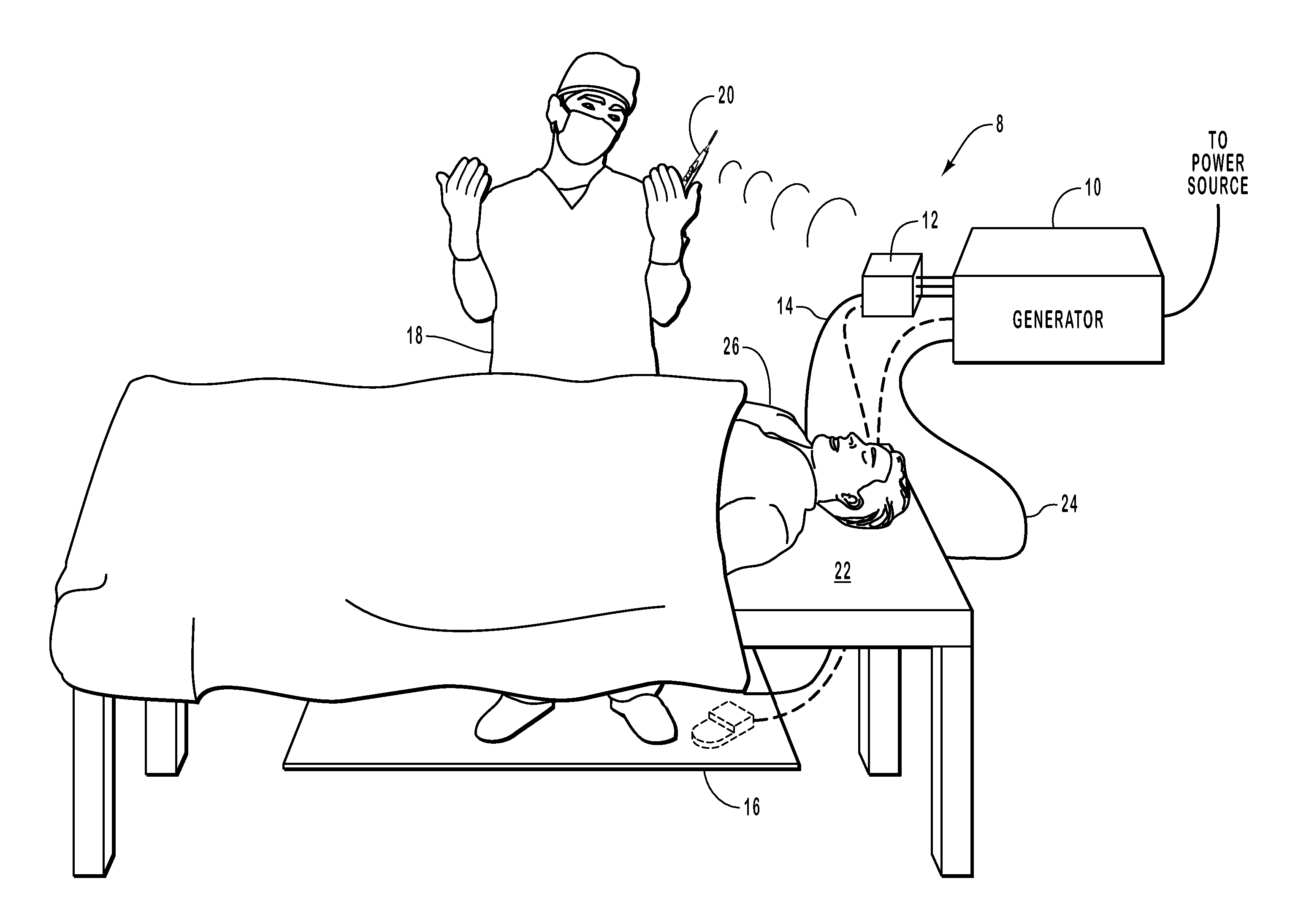
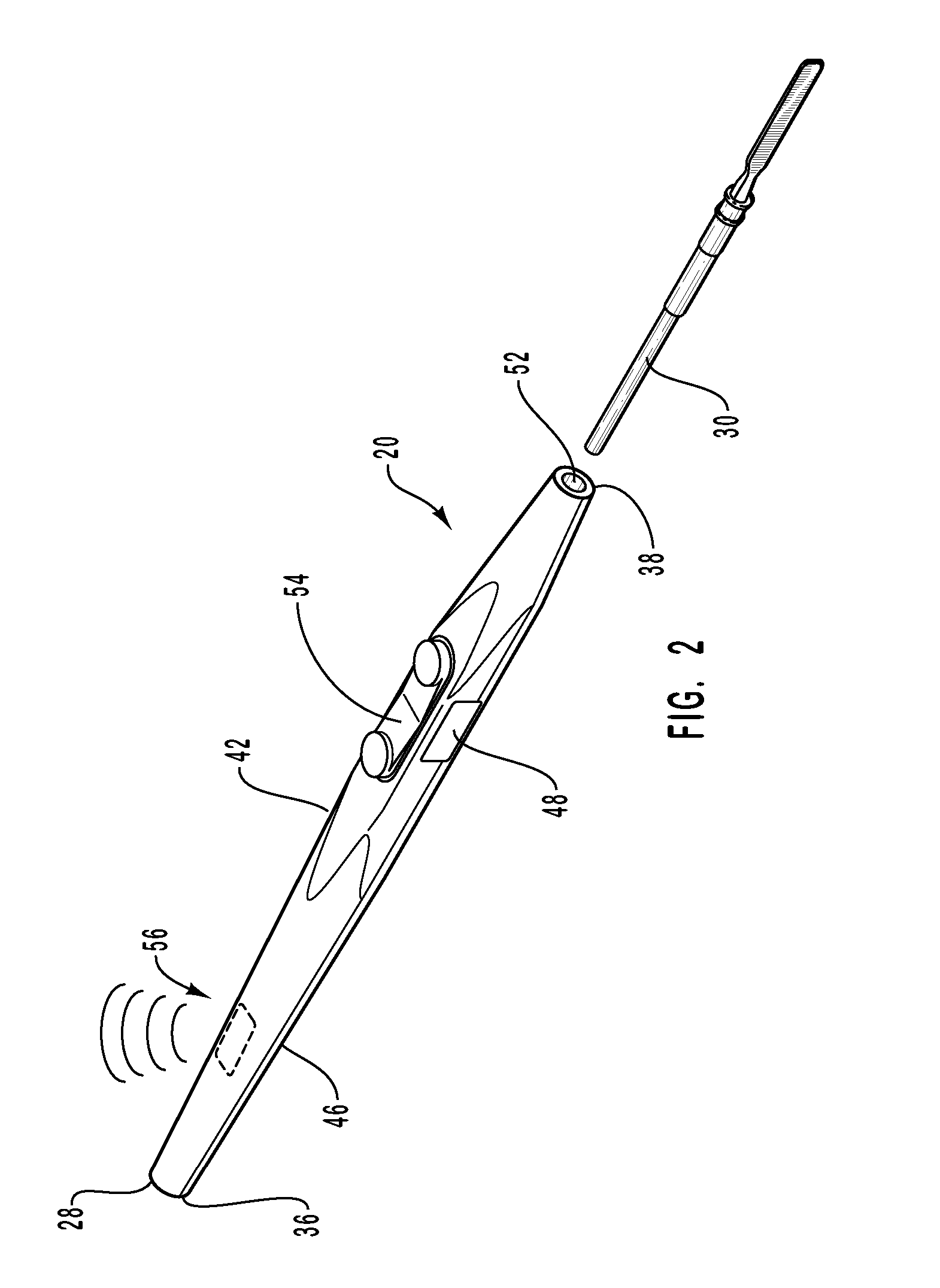
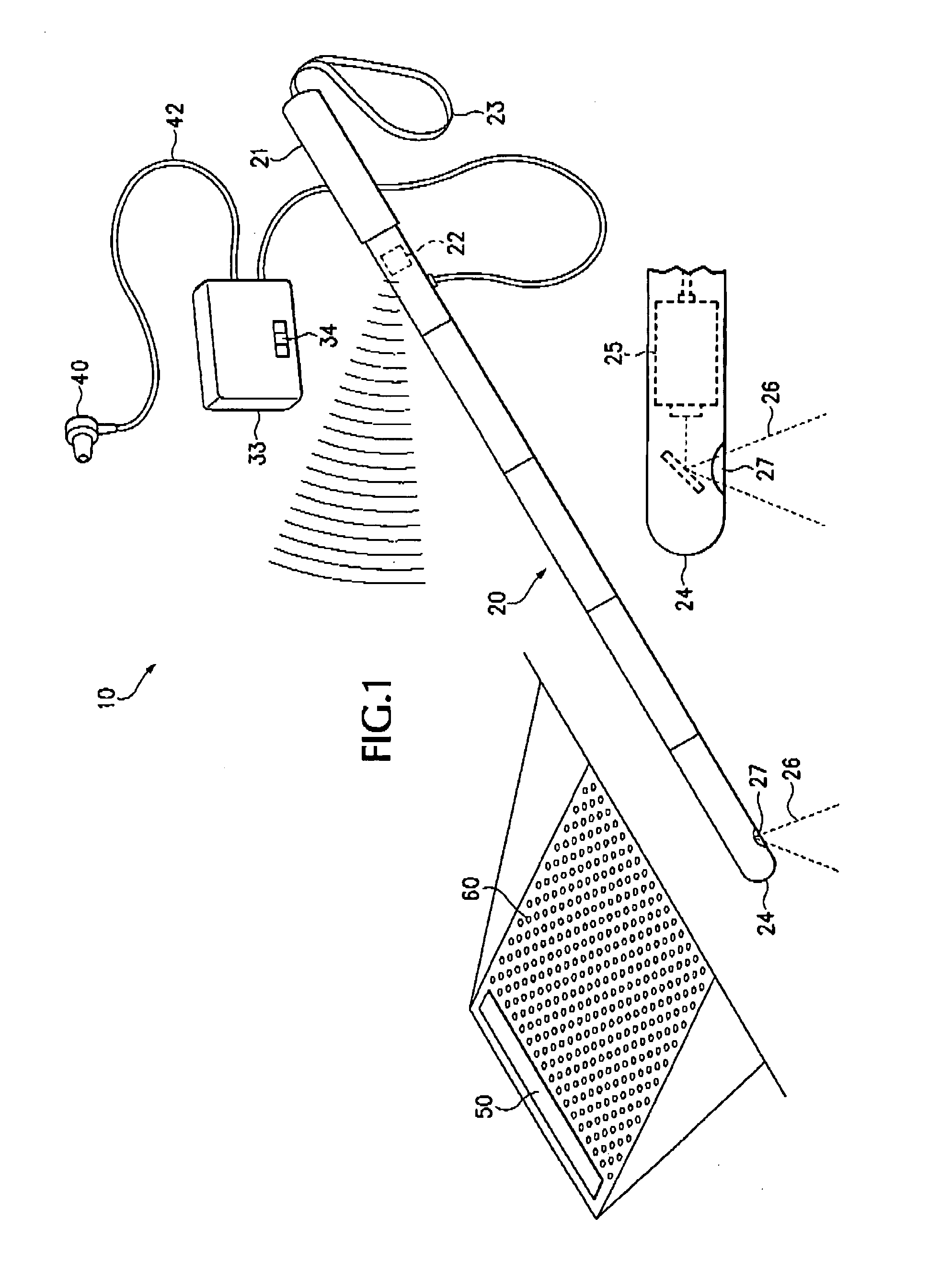
Methods, systems, and devices for performing electrosurgical procedures
ActiveUS20070060919A1Less mannerEnvironment safetySurgical instruments for heatingSurgical operationWireless control
Systems, methods, and instruments associated with controlling the operating modes of an electrosurgical instrument using control signals delivered in a wireless manner from the electrosurgical instrument to an electrosurgical generator. The electrosurgical instrument transmits wireless control signals to the electrosurgical generator to initiate delivery of electrosurgical energy. The control signals are delivered to the electrosurgical generator without the need for a conductive cord extending between the electrosurgical generator and the electrosurgical instrument. The energy is delivered to the electrosurgical instrument, in response to the wireless control signals, along a path through an electrode and the physician utilizing the electrosurgical instrument and / or a conductive path external to the physician. The electrode upon which the physician rests provides a path for the electrosurgical energy and optionally prevents burning of the physician during an electrosurgical procedure.
Owner:MEGADYNE MED PROD INC US
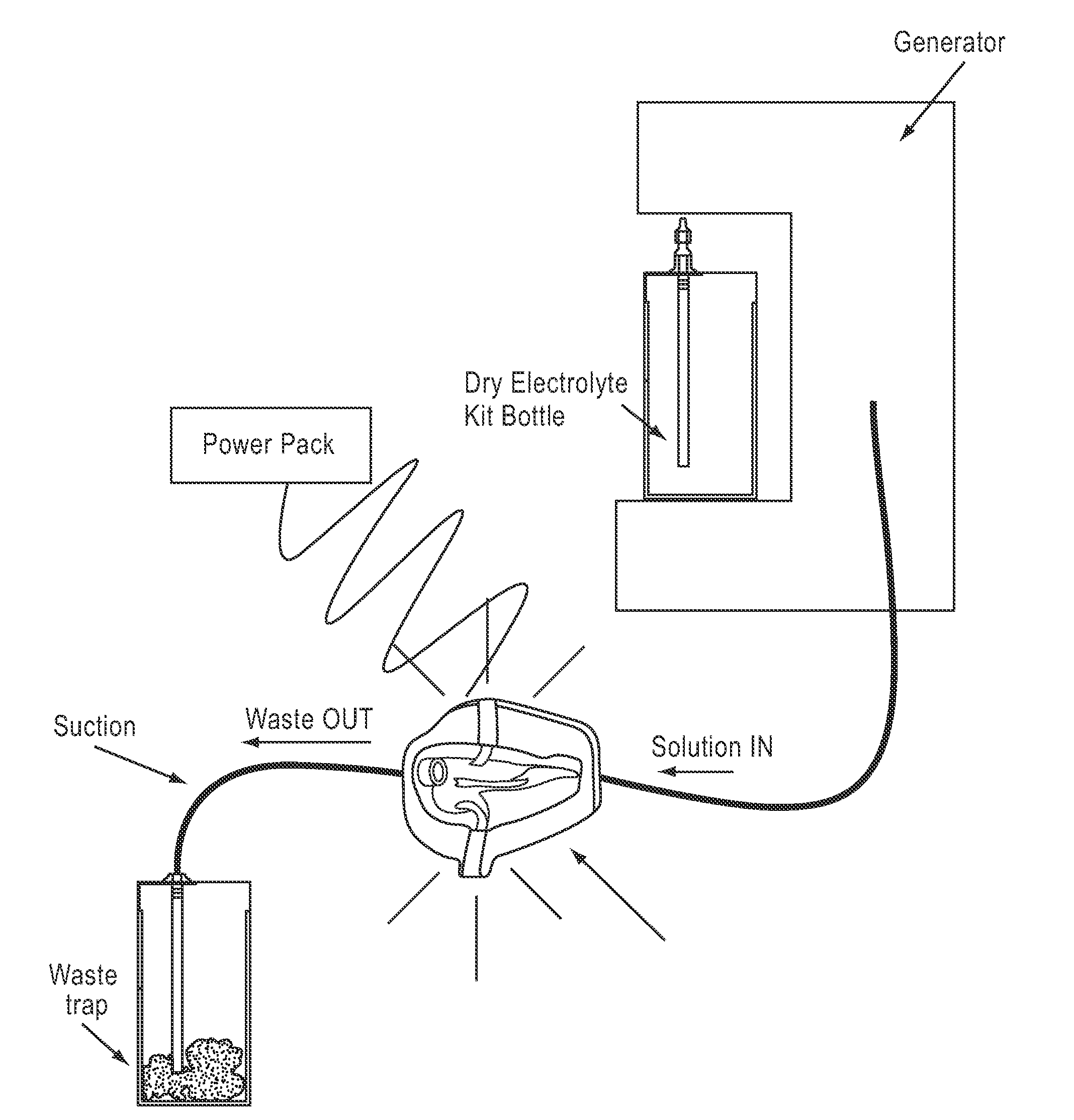
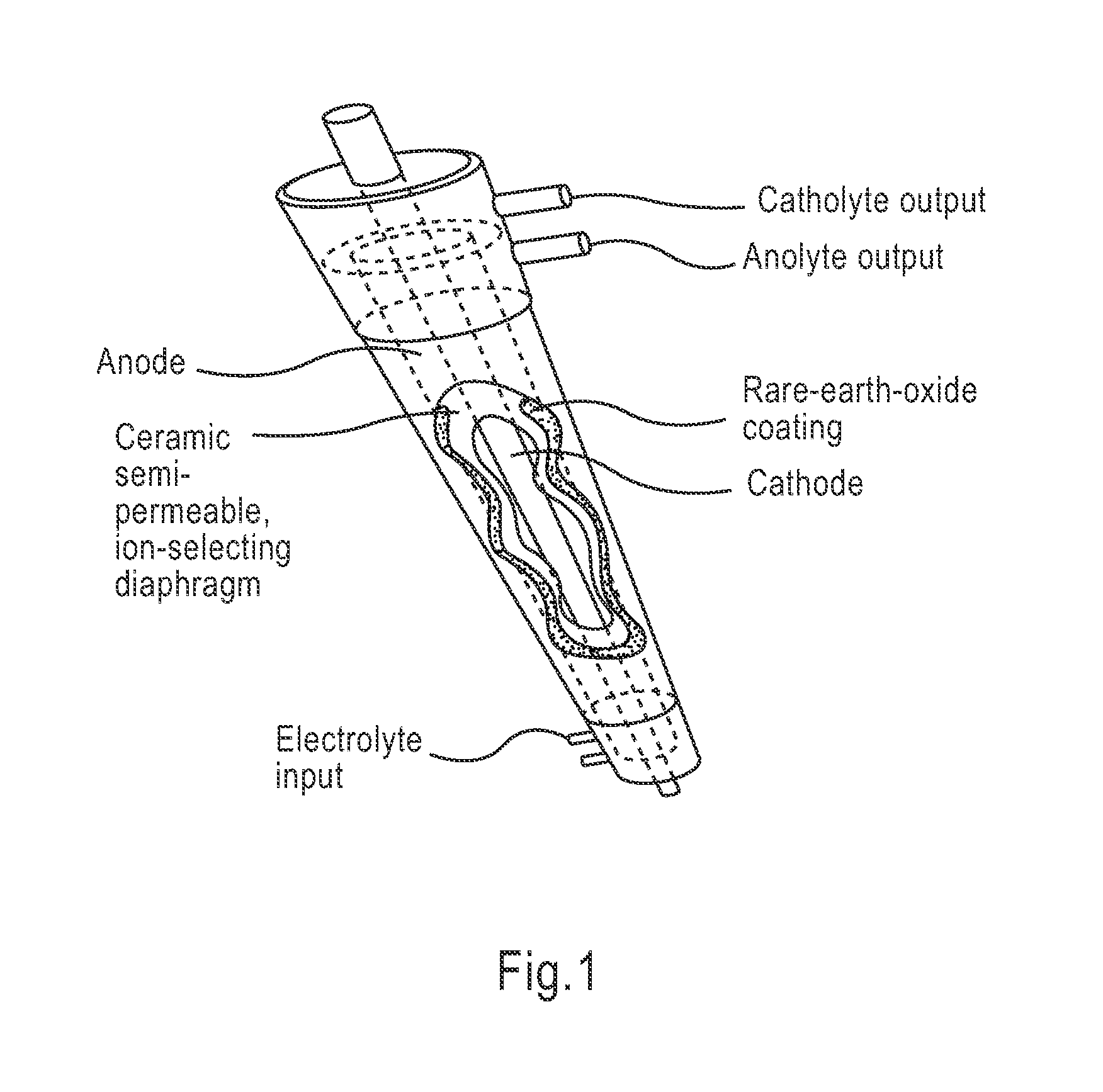
Apparatus and method for wound, cavity, and bone treatment
InactiveUS20100030132A1Quicker wound closureSafer wound care environmentElectrolysis componentsCannulasNeed treatmentBiomedical engineering
The present invention provides a treatment apparatus. The apparatus contains a reservoir or generator for a treatment solution, a mechanism for delivering the treatment solution to a wound site, and a mechanism for applying the solution to a wound, tissue, bone or surgical cavity for treatment. The apparatus may apply the solution (e.g., a solution containing hypohalous acid) with, for example, an occlusive wound dressing, pulsative lavage device, hydrotherapy, hydrosurgical device, and / or ultrasound. A waste container may be operably connected to the apparatus for collecting waste from the wound by run-off, or by applying negative pressure (e.g. a vacuum). Because the apparatus of the invention can optionally be portable or mobile, the invention is suitable for use in hospitals and nursing homes, as well as for home wound care. The invention also provides a method for treating a wound (or other area needing treatment), and / or for reducing wound bioburden, by supplying a hypochlorous acid solution to the site, such as a wound colonized or infected with drug resistant bacteria, before, during, or after negative pressure wound therapy.
Owner:PURICORE
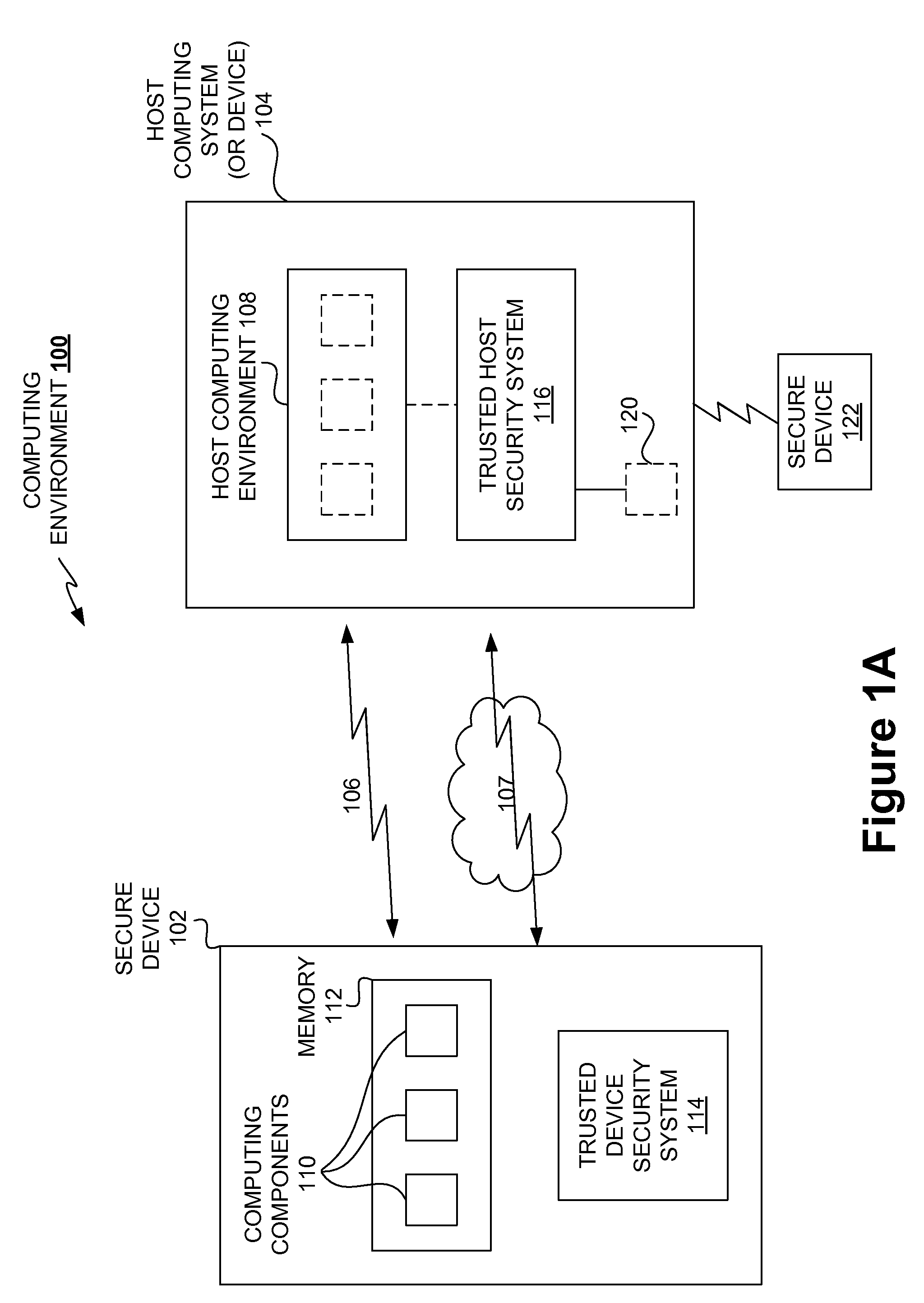
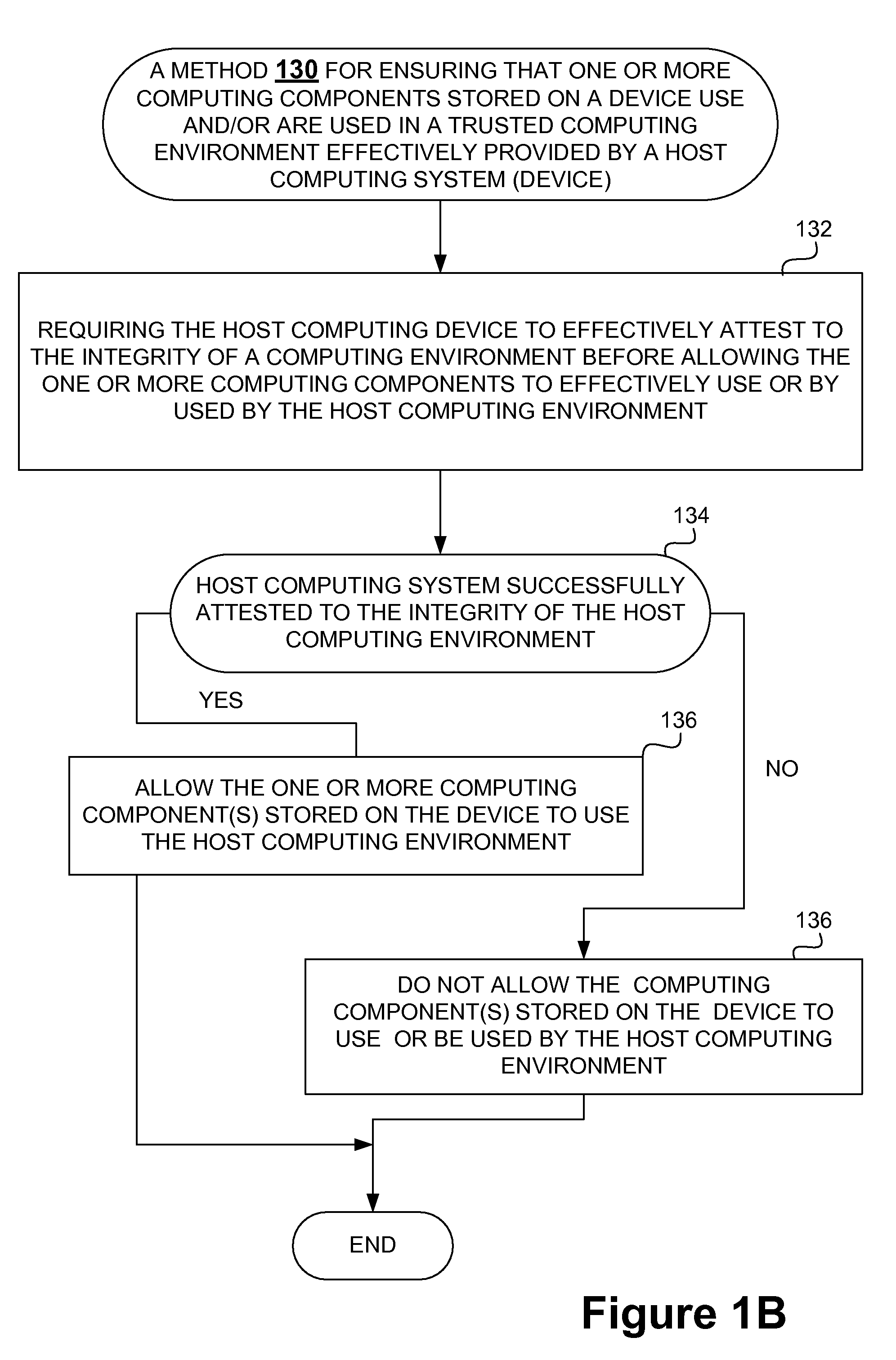
Securing stored content for trusted hosts and safe computing environments
InactiveUS20090049510A1Safe computing environmentEasy to usePublic key for secure communicationDigital data processing detailsHosting environmentComputer science
Techniques for protecting content to ensure its use in a trusted environment are disclosed. The stored content is protected against harmful and / or defective host (or hosted) environments. A trusted security component provided for a device can verify the internal integrity of the stored content and the host before it allows the content to come in contact with the host. As a counter part, a trusted security component provided for the host can verify and attest to the integrity of the host and / or specific host computing environment that can be provided for the content stored in the device. The trusted security component provided for a device effectively verify the host integrity based on the information attested to by the trusted security component provided for the host. If the trusted security component trusts the host, it allows the trusted host to provide a trusted host computing environment trusted to be safe for the content stored in the device. A trusted host can effectively provide a safe virtual environment that allows a content representing a copy (or image) of an original computing environment to operate on the host computing system to give a similar appearance as the original computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
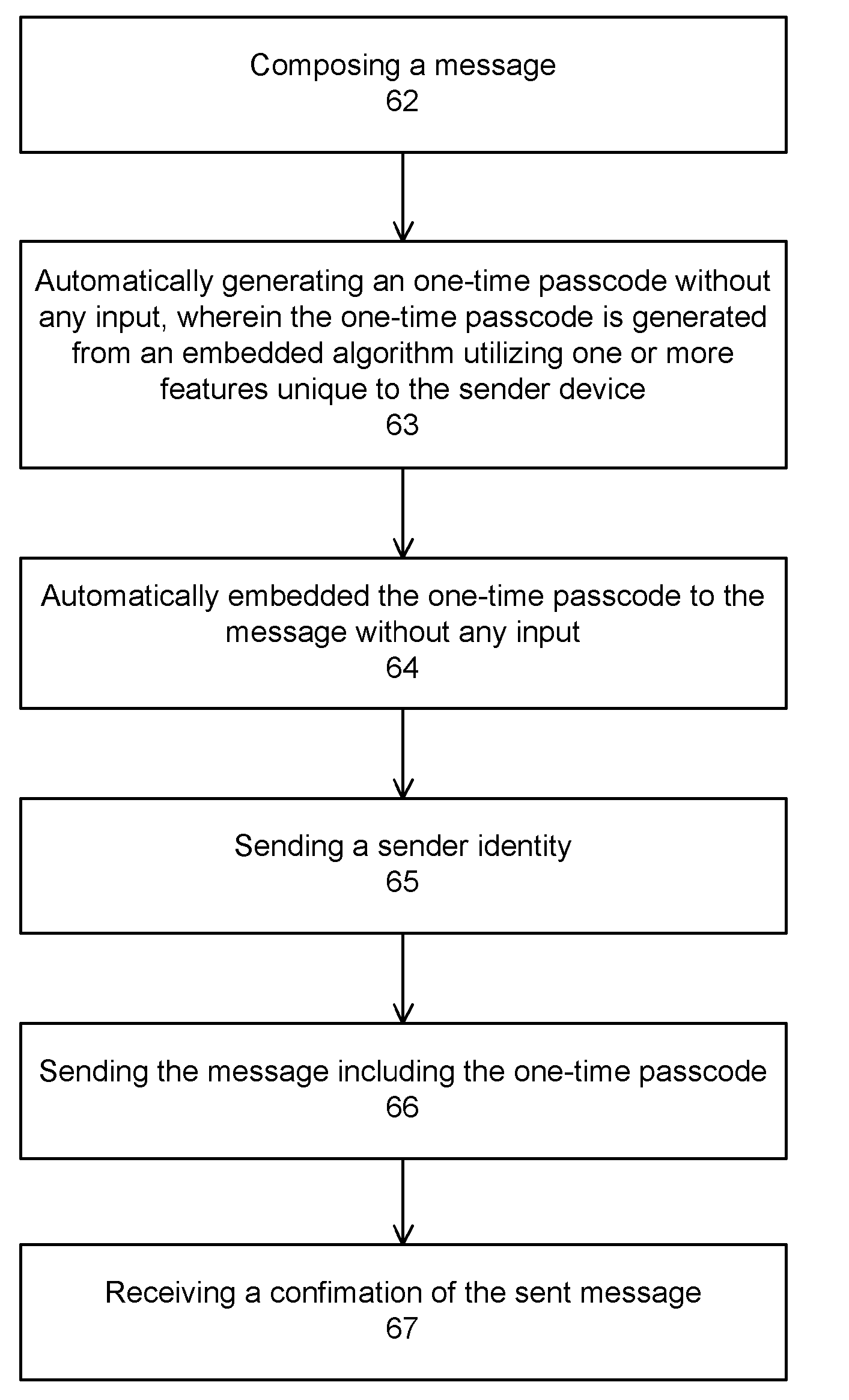
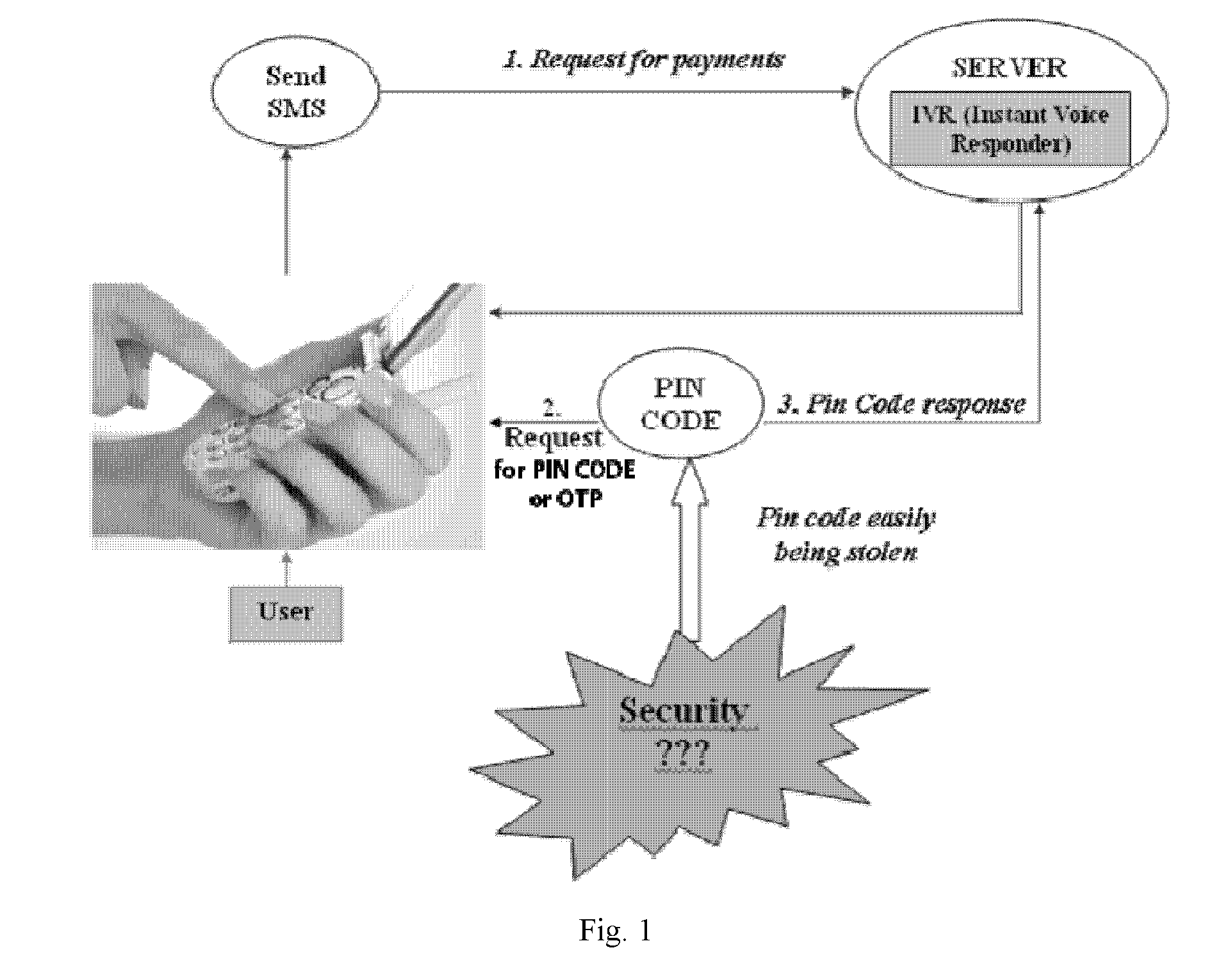
Multi-factor authentication and certification system for electronic transactions
InactiveUS20090172402A1Environment safetyImprove securityFinanceUser identity/authority verificationE-commerceOne-time password
The present invention provides computer-enable certification and authentication in, for example, e-commerce with wireless and mobile devices. The present authentication method offers ease of operation by automatically embedding a one-time passcode to the message without the sender input. A one-time key can also be used to encrypt the message, further providing transmission security. In addition, sensitive information and one-time passcode generator are pre-arranged and stored at both sender and receiver devices, avoiding information comprising in wireless environment transmission.
Owner:TRAN NGUYEN THO
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
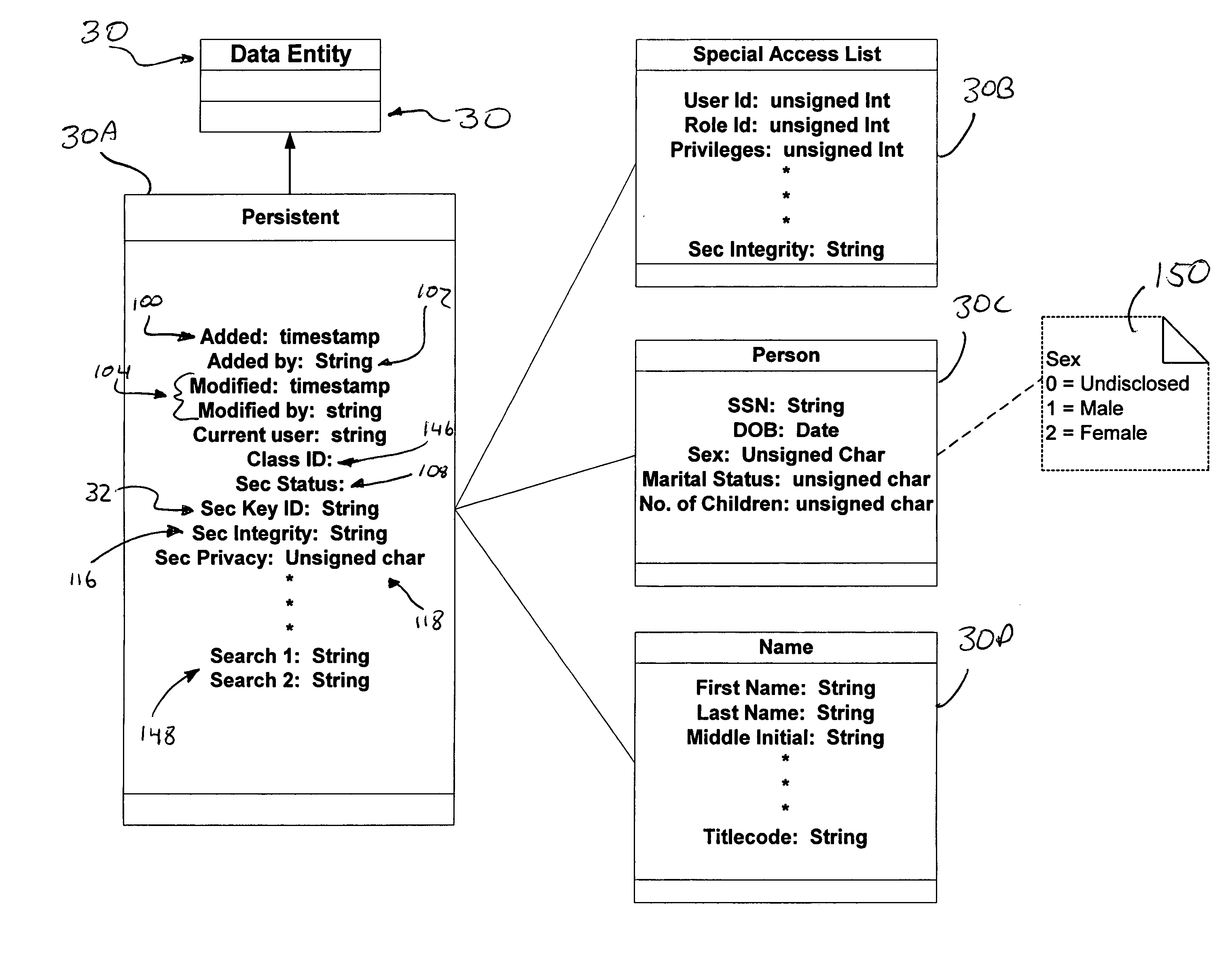
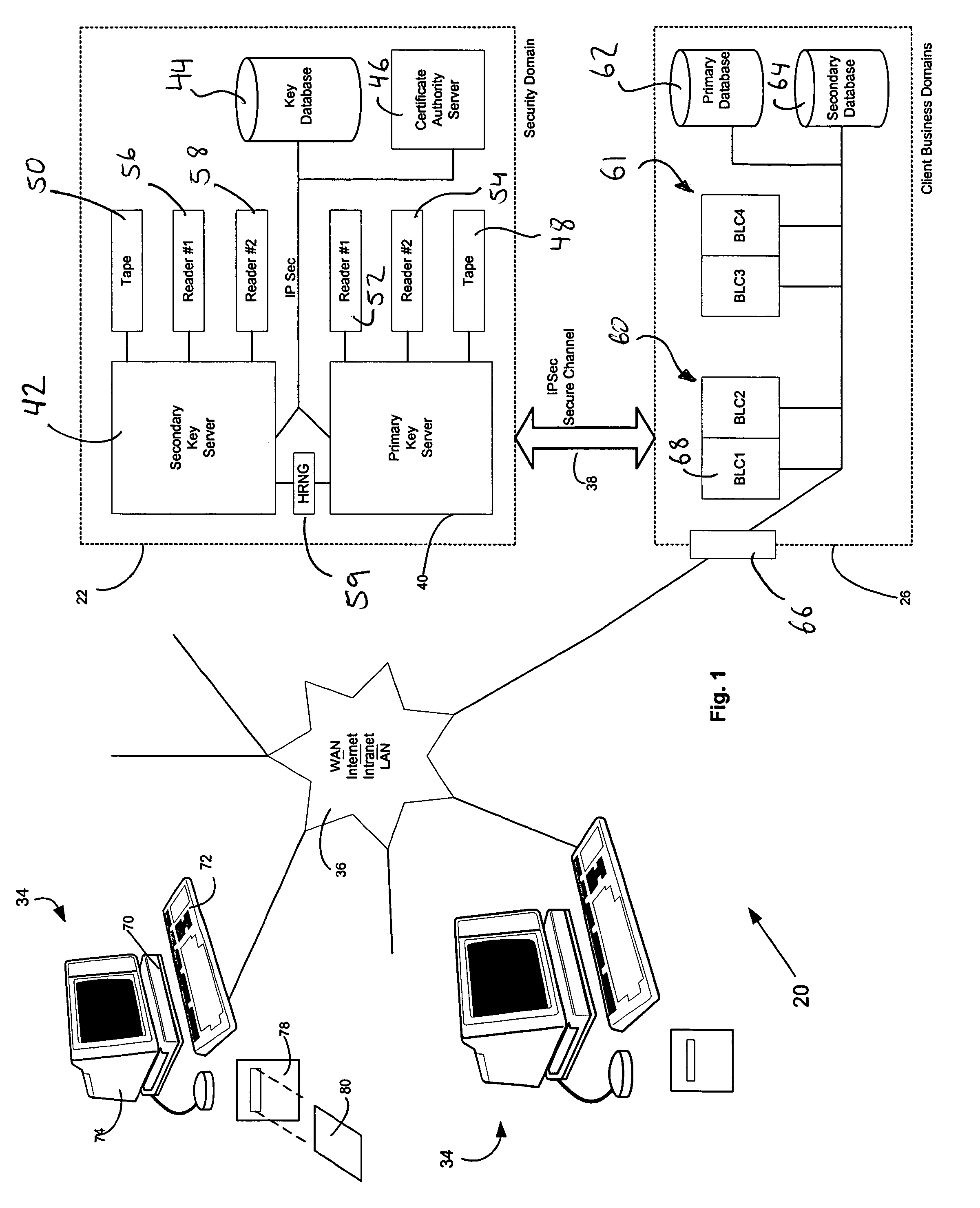
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
Vehicle safety device for reducing driver distractions
InactiveUS20120252350A1Improve securityEnvironment safetyAssess restrictionAutomatic exchangesDriver/operatorDriver Distractions
A safety device for vehicles. The device inhibits use of communication devices that run the risk of distracting a driver / operator while the vehicle is in motion. Several techniques for inhibiting use are described which can be used individually or in a complementary combinations. In one technique, a rapidly varying signal level is created local to the communication device. The variations exceed the operational limits of the system, thereby inhibiting communications. The device may be in a constant-on mode, unless it detects an attempt to make a communication classified as appropriate. Such a device may inhibit short messages, such as “text” messages and may also allow or, in some embodiments, place emergency calls.
Owner:STEINMETZ ALLAN +2
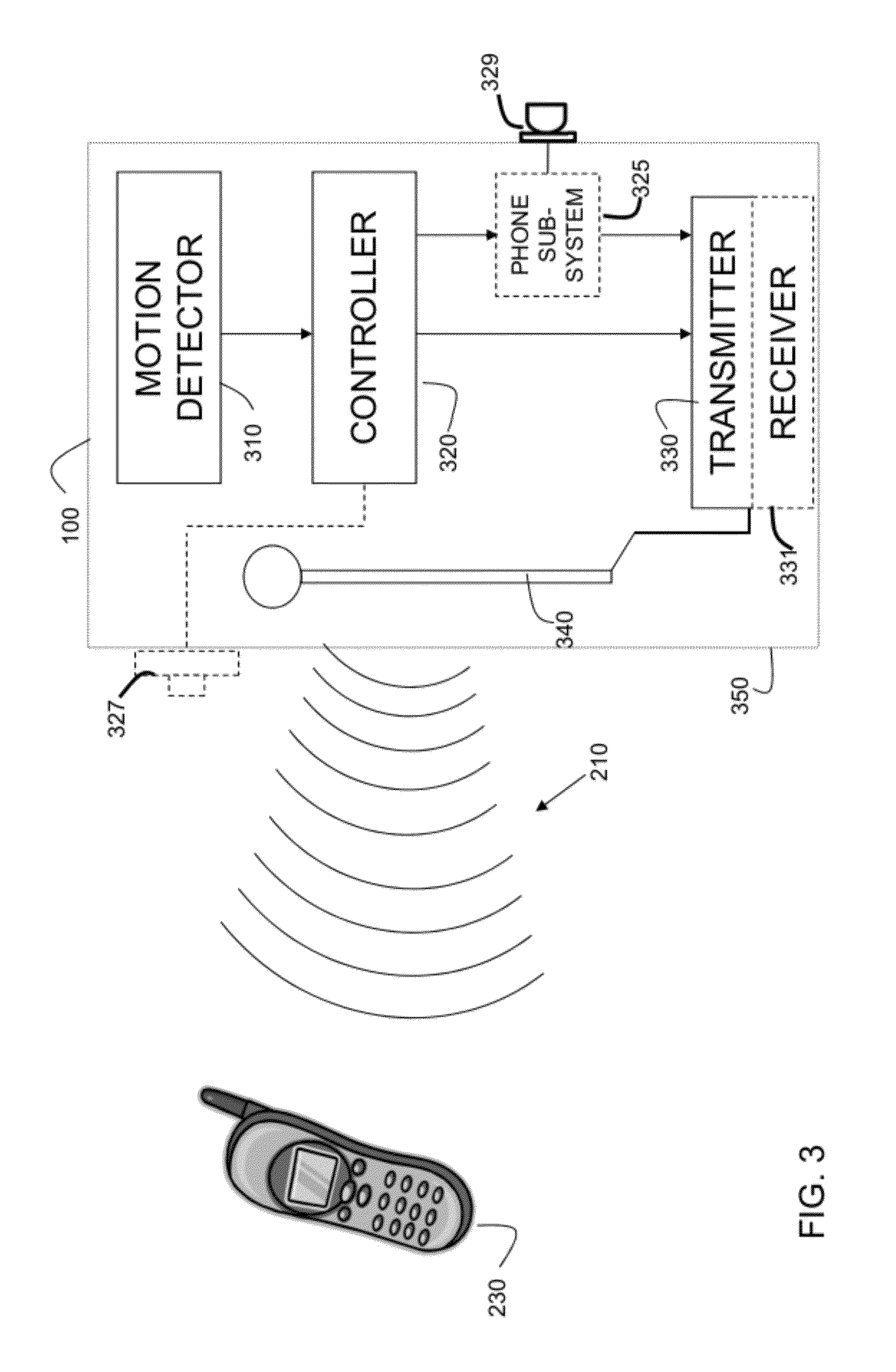
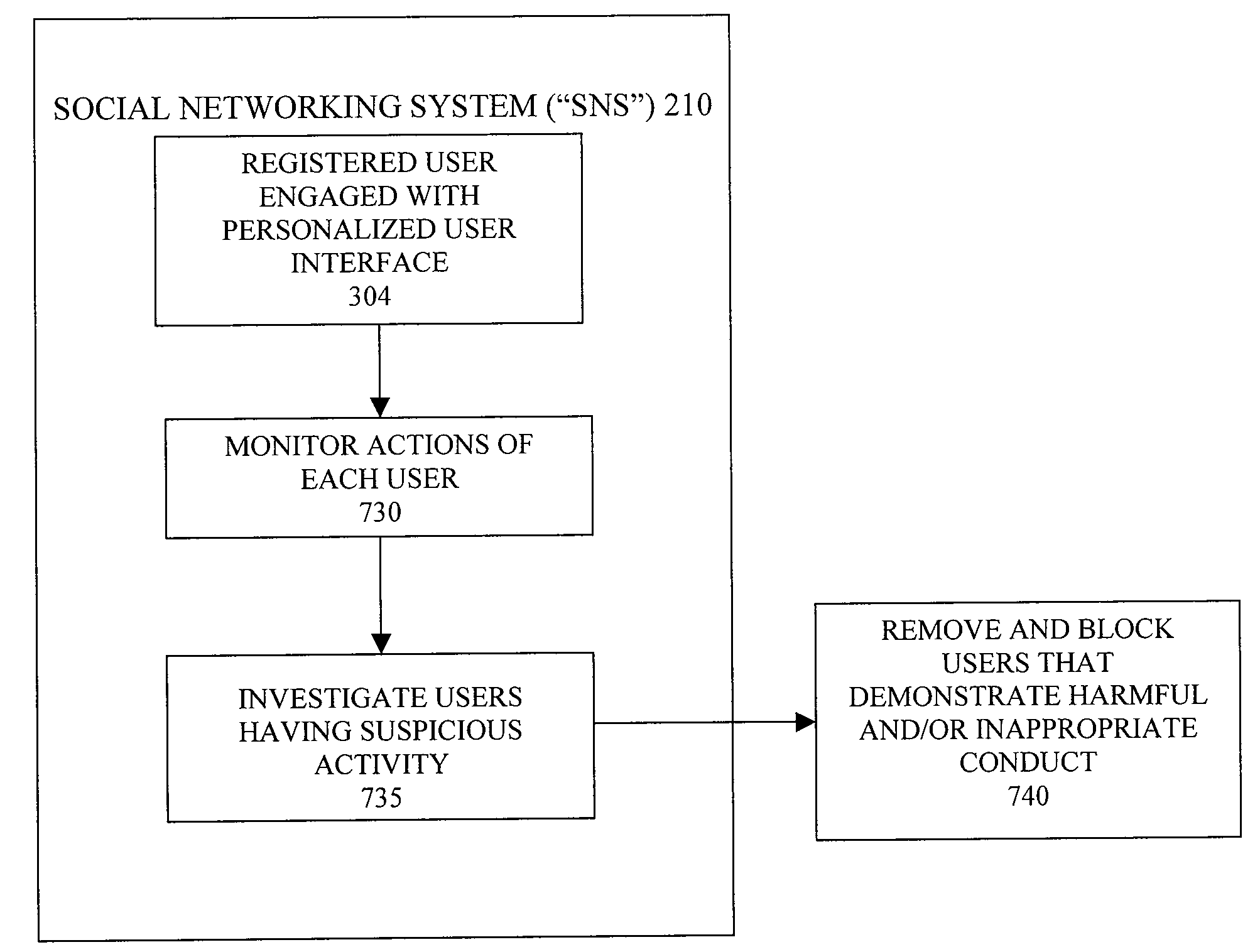
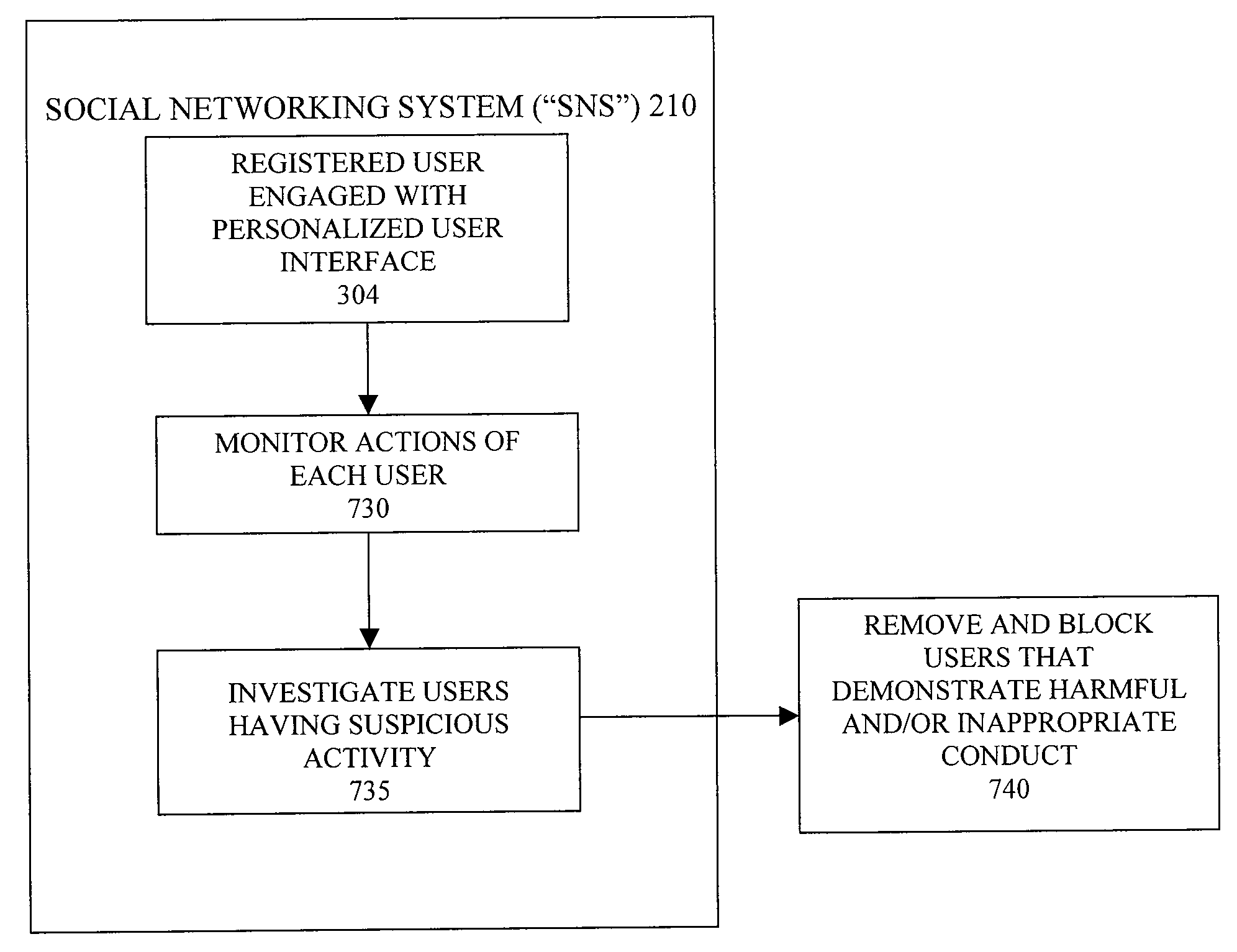
Secure Social Networking System with Anti-Predator Monitoring
InactiveUS20080282324A1Strengthen restrictionsSafe and secureAdvertisementsDigital data processing detailsInternet privacySocial web
The invention provides a method for managing an online social network, the method including the steps of: a) identifying patterns associated with inappropriate user activity; a) monitoring the online actions of at least one user of the social network; b) evaluating online actions taken by the at least one user; and c) comparing the online actions to the identified patterns associated with inappropriate activity.
Owner:HOAL MARY KAY
System and method for executing an application on a secured run-time environment
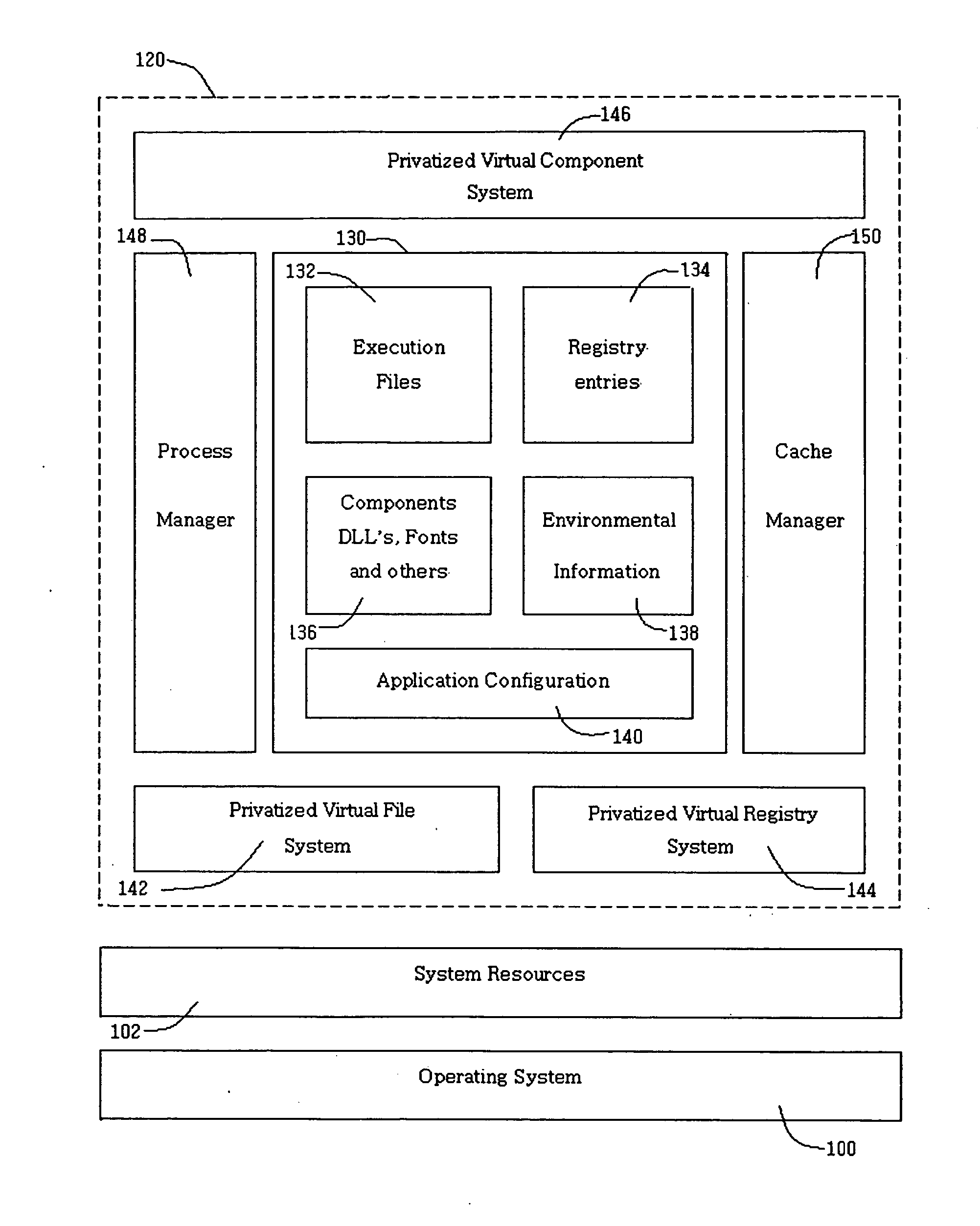
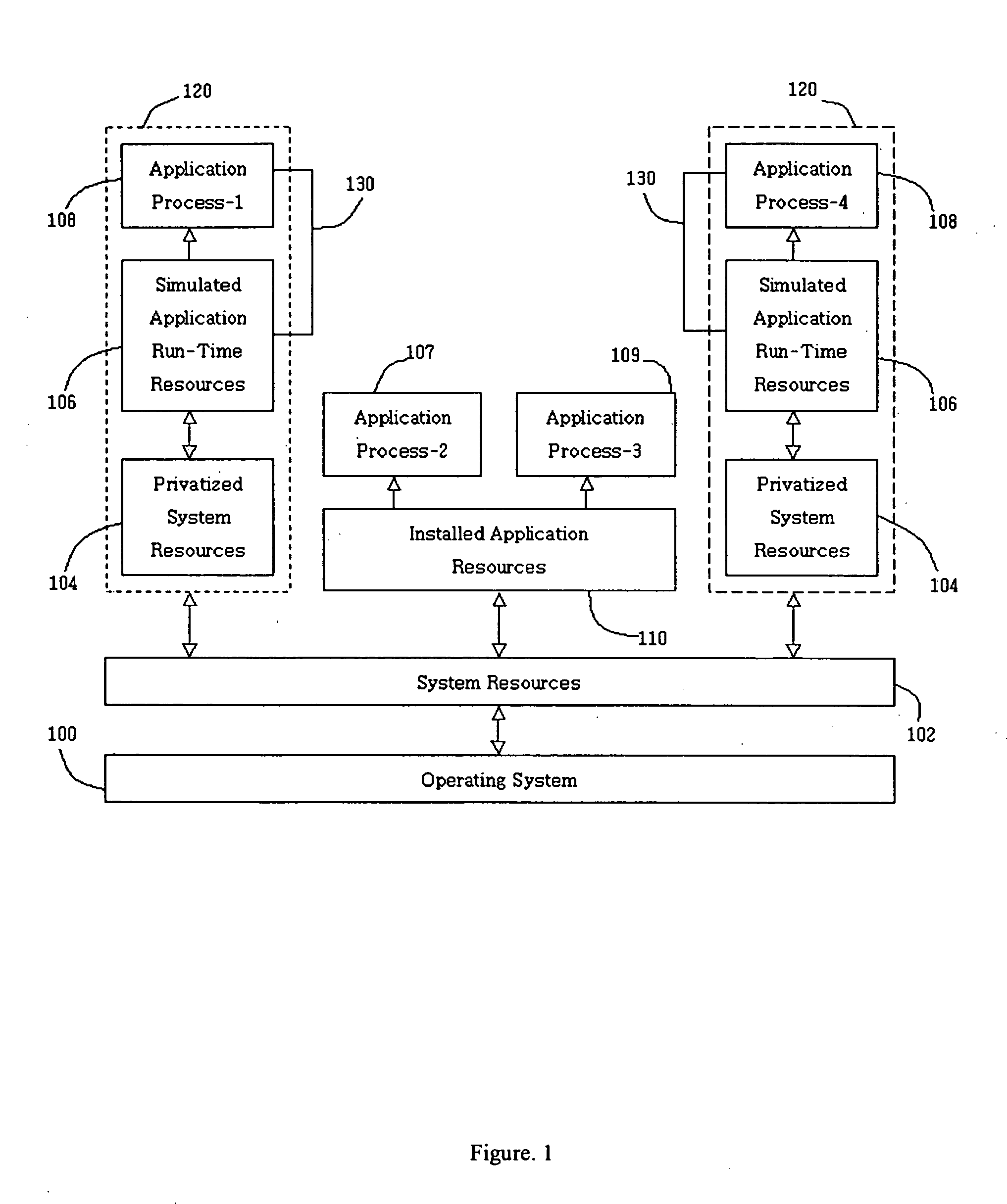
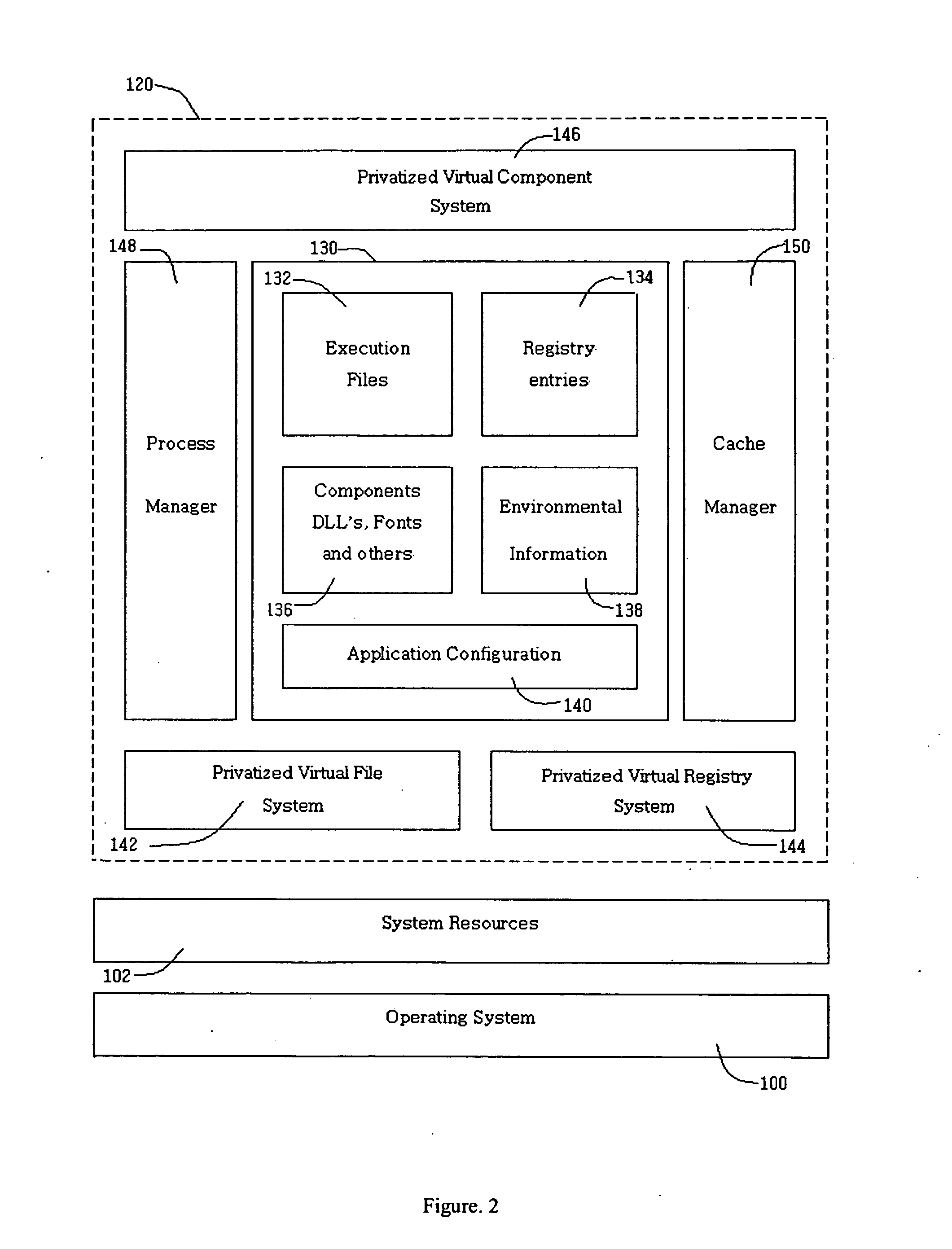
InactiveUS20050114870A1Eliminates application conflictEnvironment safetyPlatform integrity maintainanceMulti user environmentApplication software
An application wrapper system and method provide a technique for privatizing application software resources from an operating system shared resources. The present invention allows the application software to execute in a secured run-time environment. The preferred embodiments of the present invention eliminates application conflict, protects operating system resources, provides multiple instance run-time for instance made to execute single instance and provides multi-user environment.
Owner:SOFTONNET
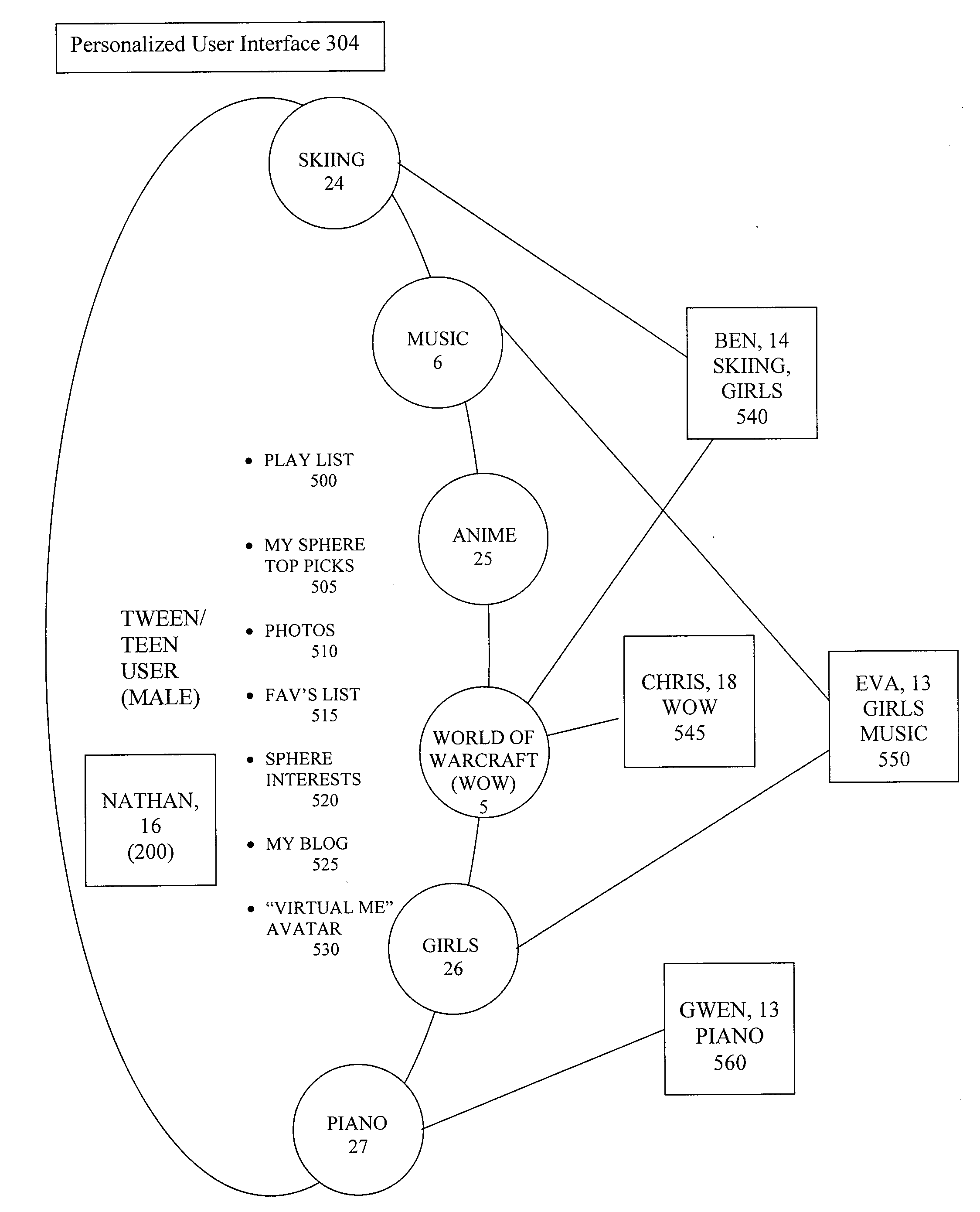
Social Networking System
InactiveUS20080281622A1Strengthen restrictionsSafe and secureAdvertisementsKnowledge representationSocial webData science
The invention provides a method of managing an online social network for peer interactions, the method comprising: a) creating at least one sphere for users to associate over a common interest; b) identifying patterns associated with activity indicative of the common interest; c) monitoring the online actions of at least one user of the social network; d) evaluating the online actions taken by the at least one user; and e) comparing the online actions to the identified patterns associated with interest in the sphere category.
Owner:HOAL MARY KAY
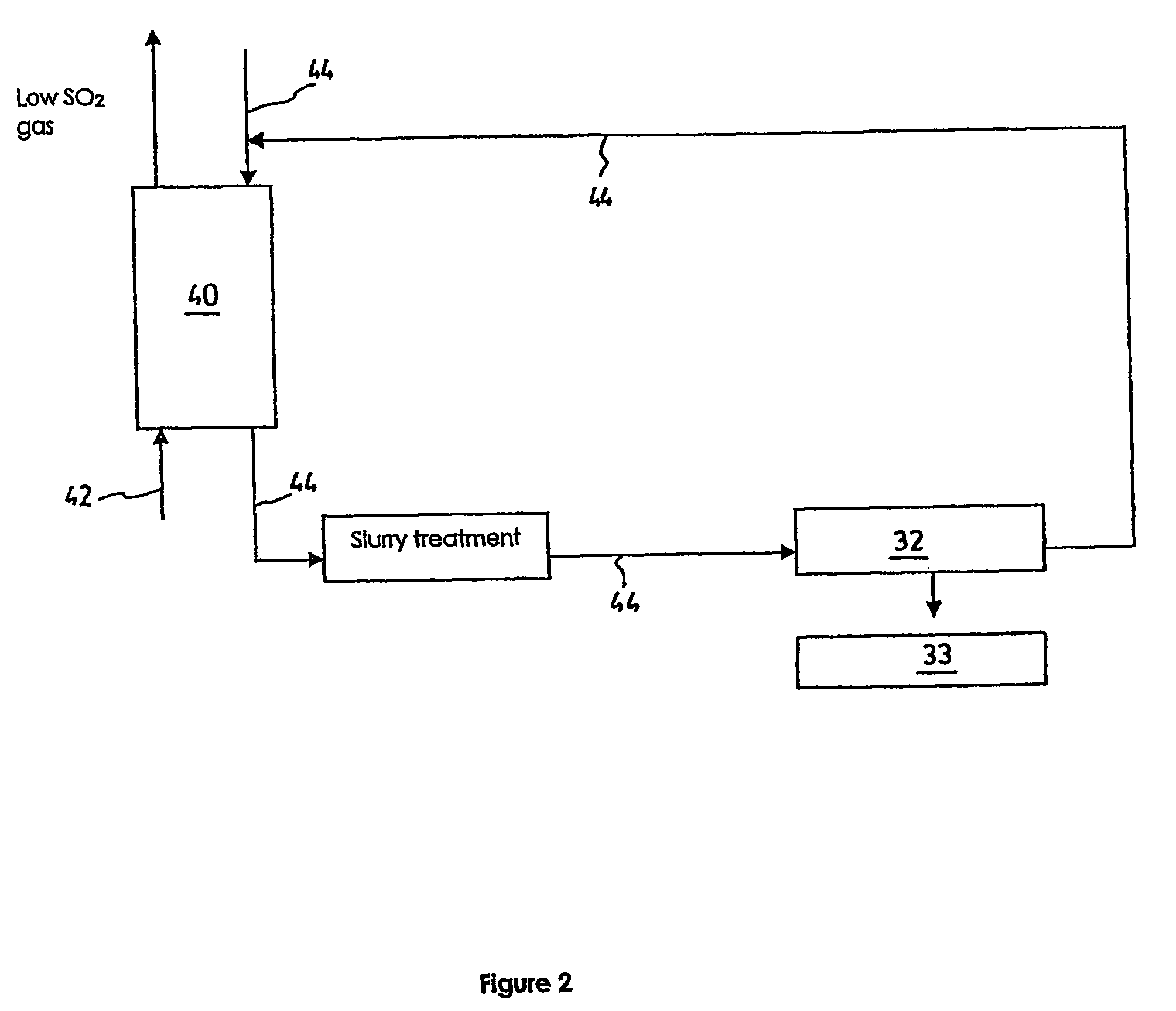
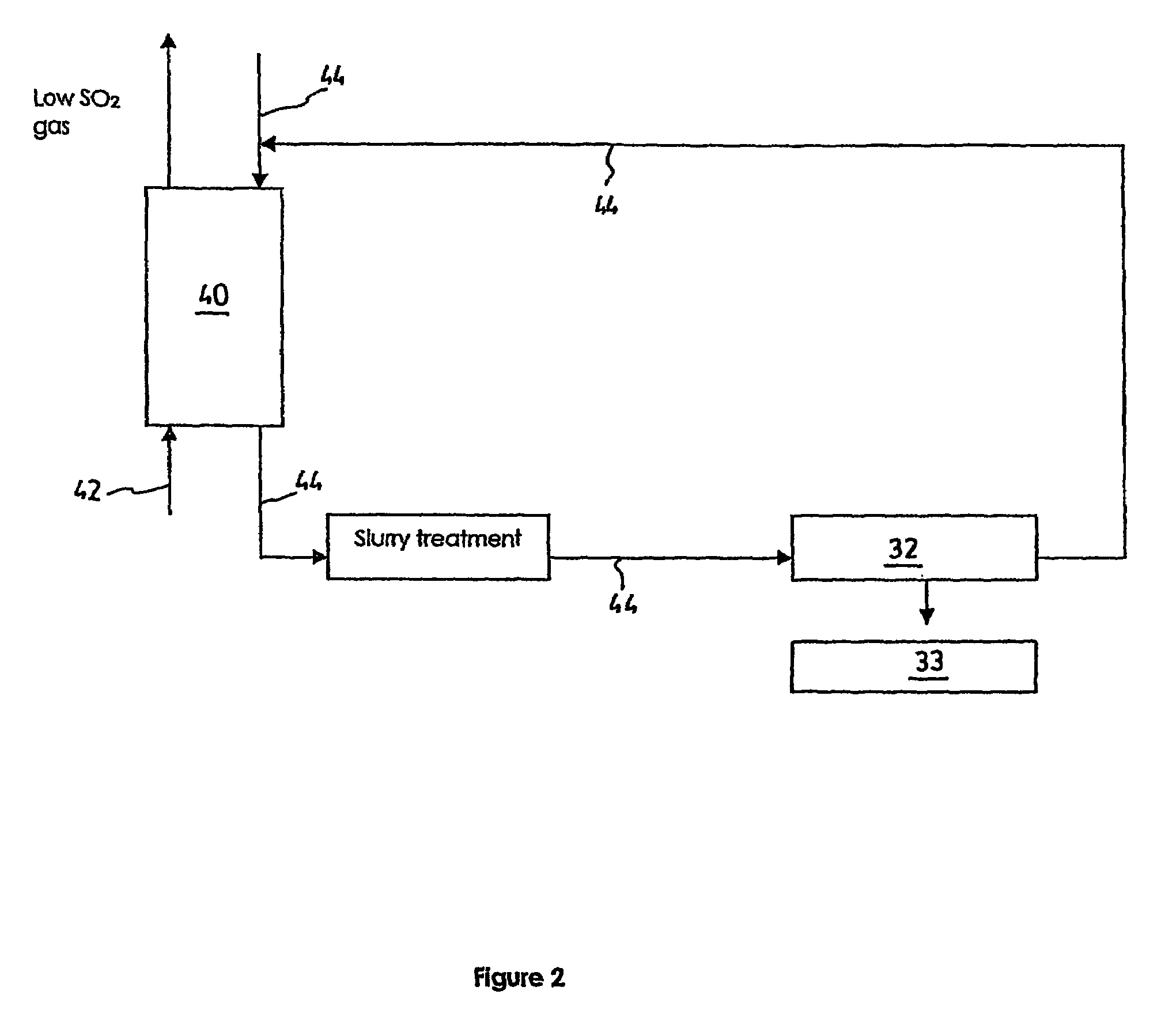
Process and a plant for recycling carbon dioxide emissions from power plants into useful carbonated species
ActiveUS20060048517A1Reduce CO2 emissionIncrease energy efficiencyCalcium/strontium/barium carbonatesGas turbine plantsCarbonationExhaust gas
A process is disclosed for recycling carbon dioxide emissions from a fossil-fuel power plant into useful carbonated species The process primarily comprises the steps of: a) burning the fossil fuel, thereby generating heat and a hot exhaust gas containing CO2; and b) converting the heat into energy. The process is characterized in that it further comprises the steps of: c) cooling the exhaust gas; and d) biologically transforming the CO2 contained in the cooled exhaust gas into carbonated species, thereby obtaining a low CO2 exhaust gas and producing useful carbonated species. The low CO2 exhaust gas obtained in step d) can be released in the atmosphere without increasing the problem of greenhouse effect.
Owner:SAIPEM SPA
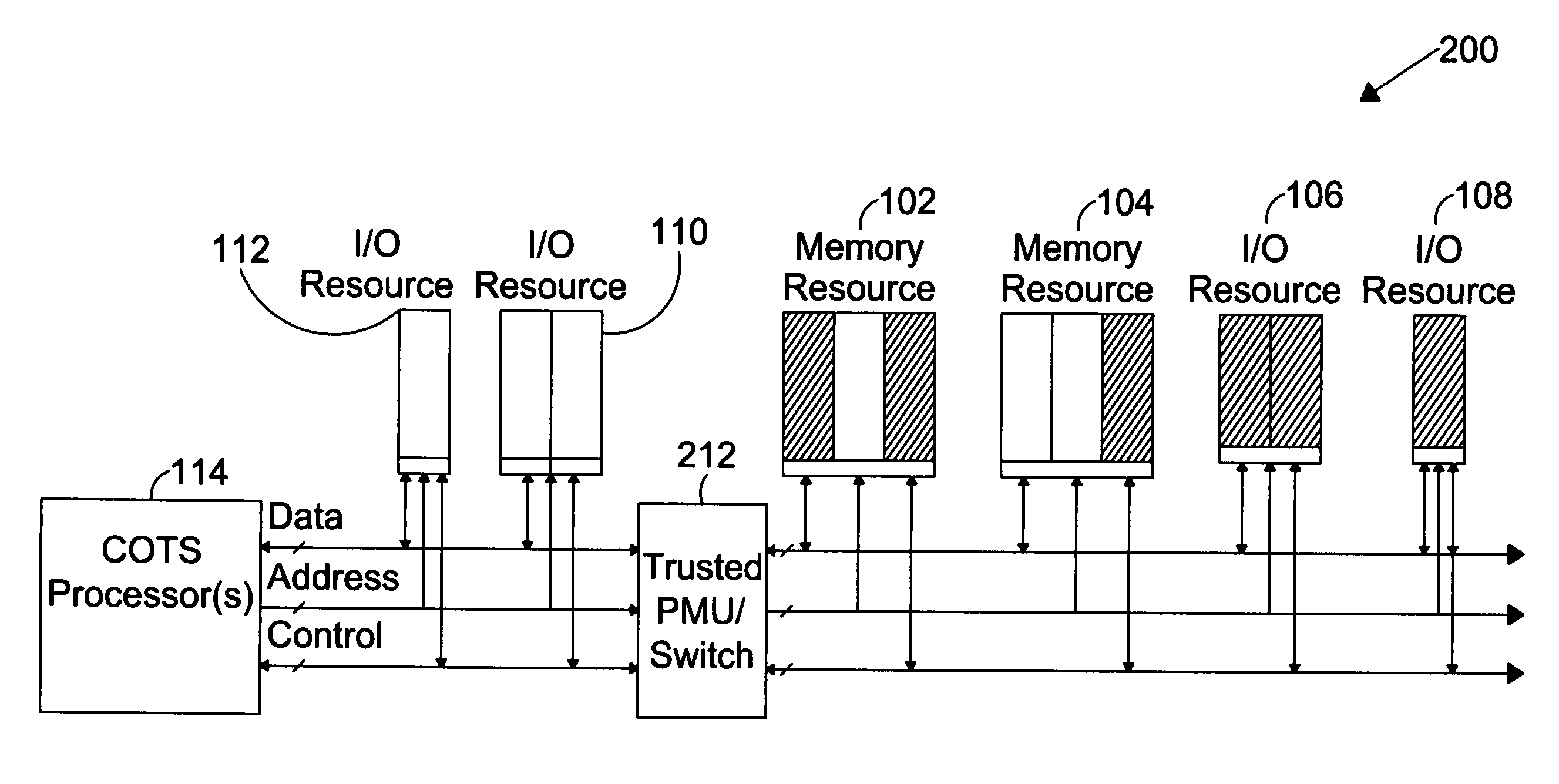
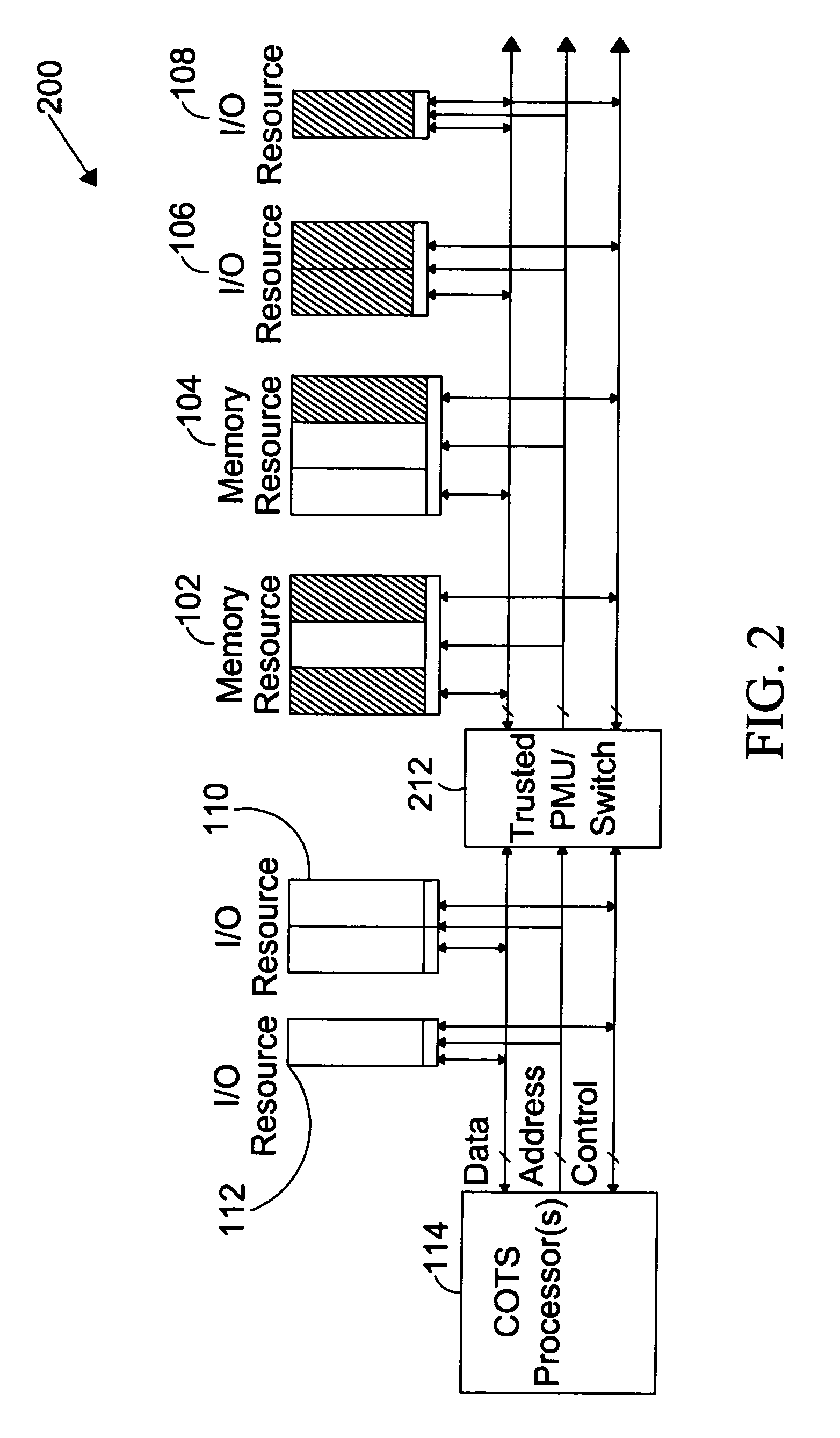
System for providing secure and trusted computing environments
ActiveUS7716720B1Provide partEnvironment safetyDigital data processing detailsUser identity/authority verificationTrusted ComputingComputer module
The present invention is directed to a system for providing a trusted environment for untrusted computing systems. The system may include a HAC subsystem managing shared resources and a trusted bus switch for controlling a COTS processor to access the shared resources. The shared resources such as memory and several I / O resources reside on the trusted side of the trusted bus switch. Alternatively, the system may include a SCM as an add-on module to an untrusted host environment. Only authenticated applications including COTS OS execute on the SCM while untrusted applications execute on the untrusted host environment. The SCM may control secure resource access from the untrusted host through a plug-in module interface. All secure resources may be maintained on the trusted side of the plug-in module interface.
Owner:ROCKWELL COLLINS INC
System and method for efficiently transferring media across firewalls
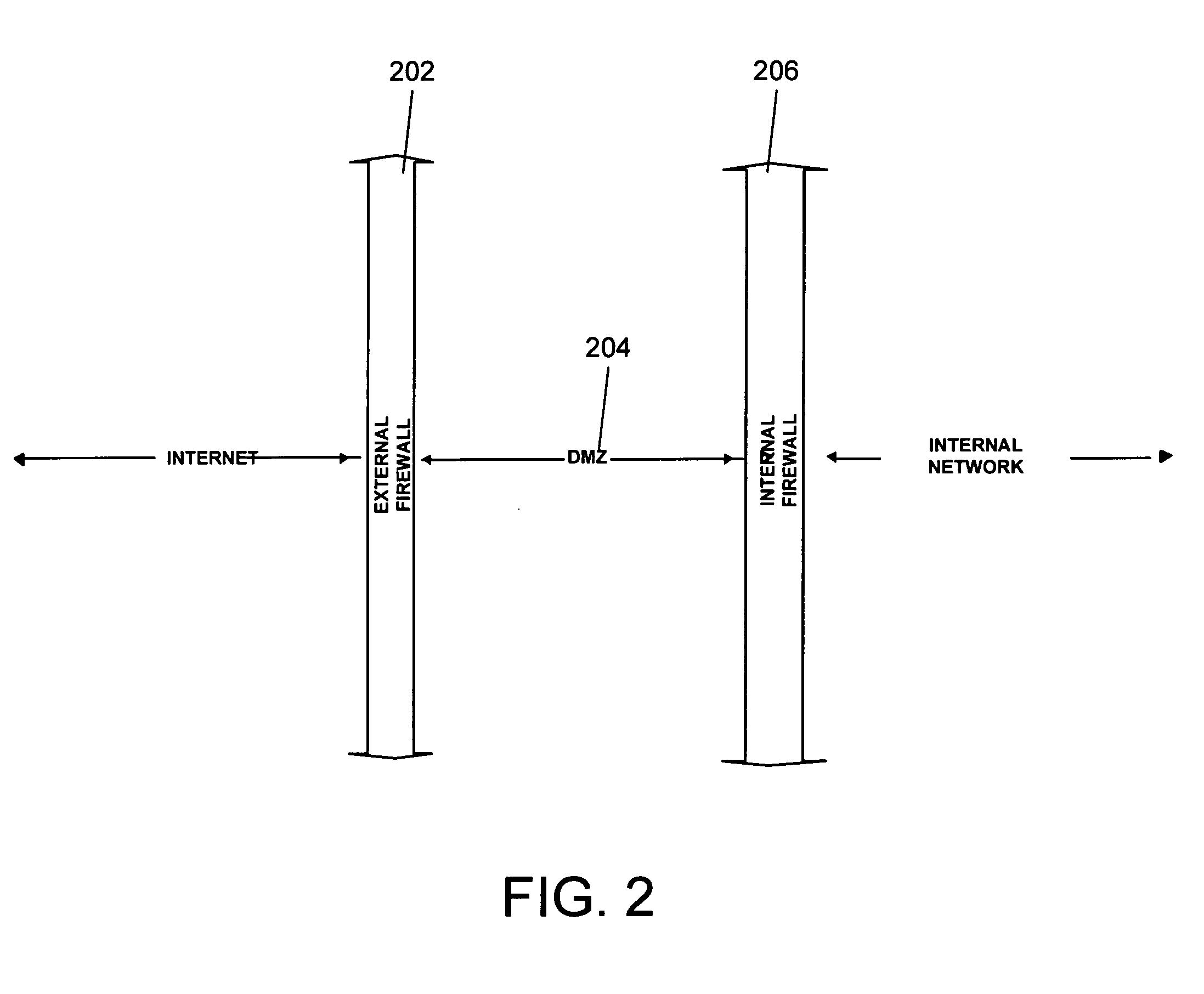
InactiveUS20050198499A1Secure network environmentEnvironment safetyMultiple digital computer combinationsProgram controlTime ProtocolNetsniff-ng
Enabling media (audio / video) scenarios across firewalls typically requires opening up multiple UDP ports in an external firewall. This is so because RTP (Real Time Protocol, RFC 1889), which is the protocol used to carry media packets over IP network, requires a separate UDP receive port for each media source. Opening up multiple media ports on the external firewall is something that administrators are not comfortable doing as they consider it security vulnerability. The system and method according to the invention provides an alternate mechanism which changes RTP protocol a little and achieves a goal of traversing firewalls for media packets using a fixed number, namely two, of UDP ports.
Owner:MICROSOFT TECH LICENSING LLC
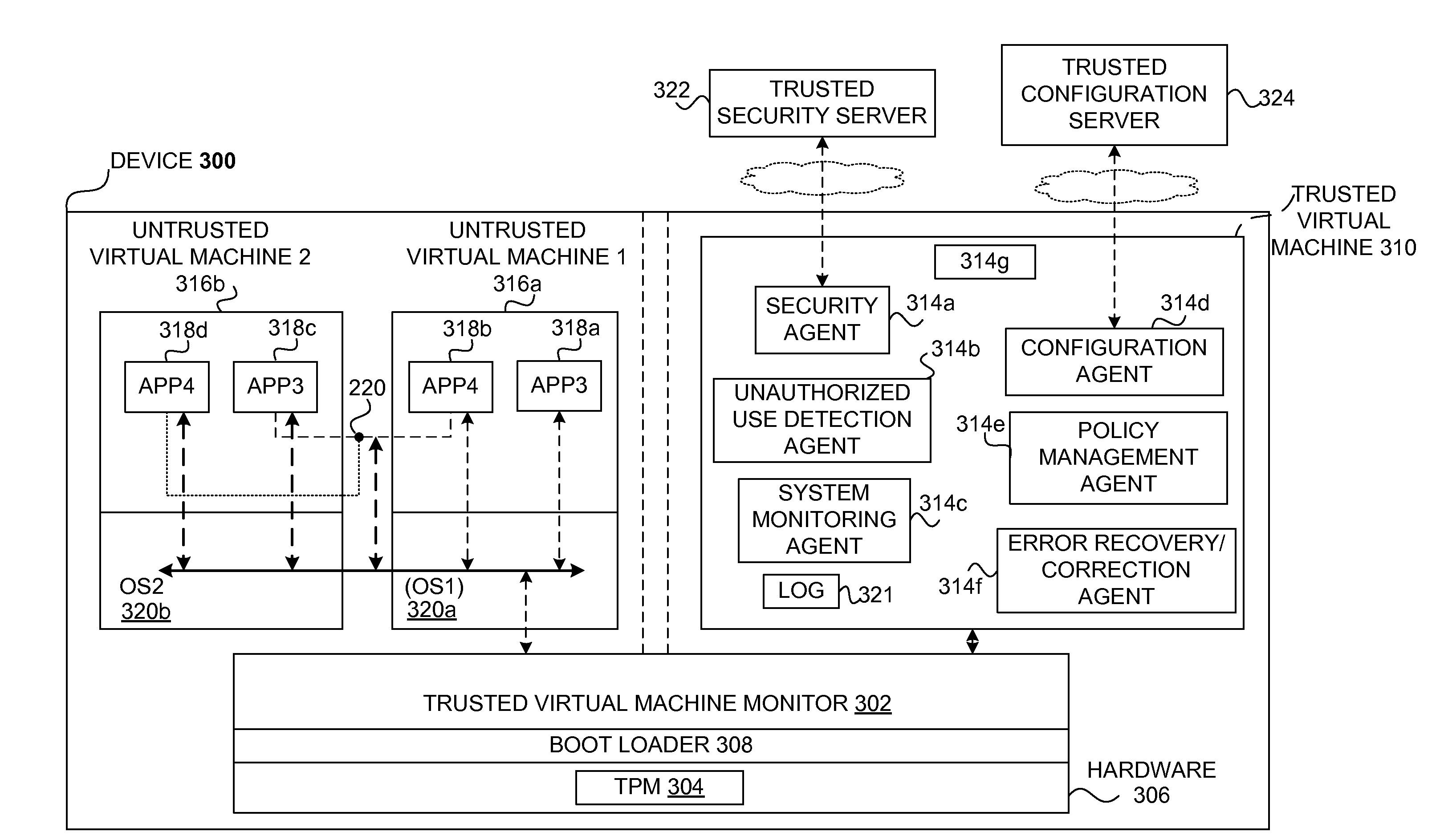
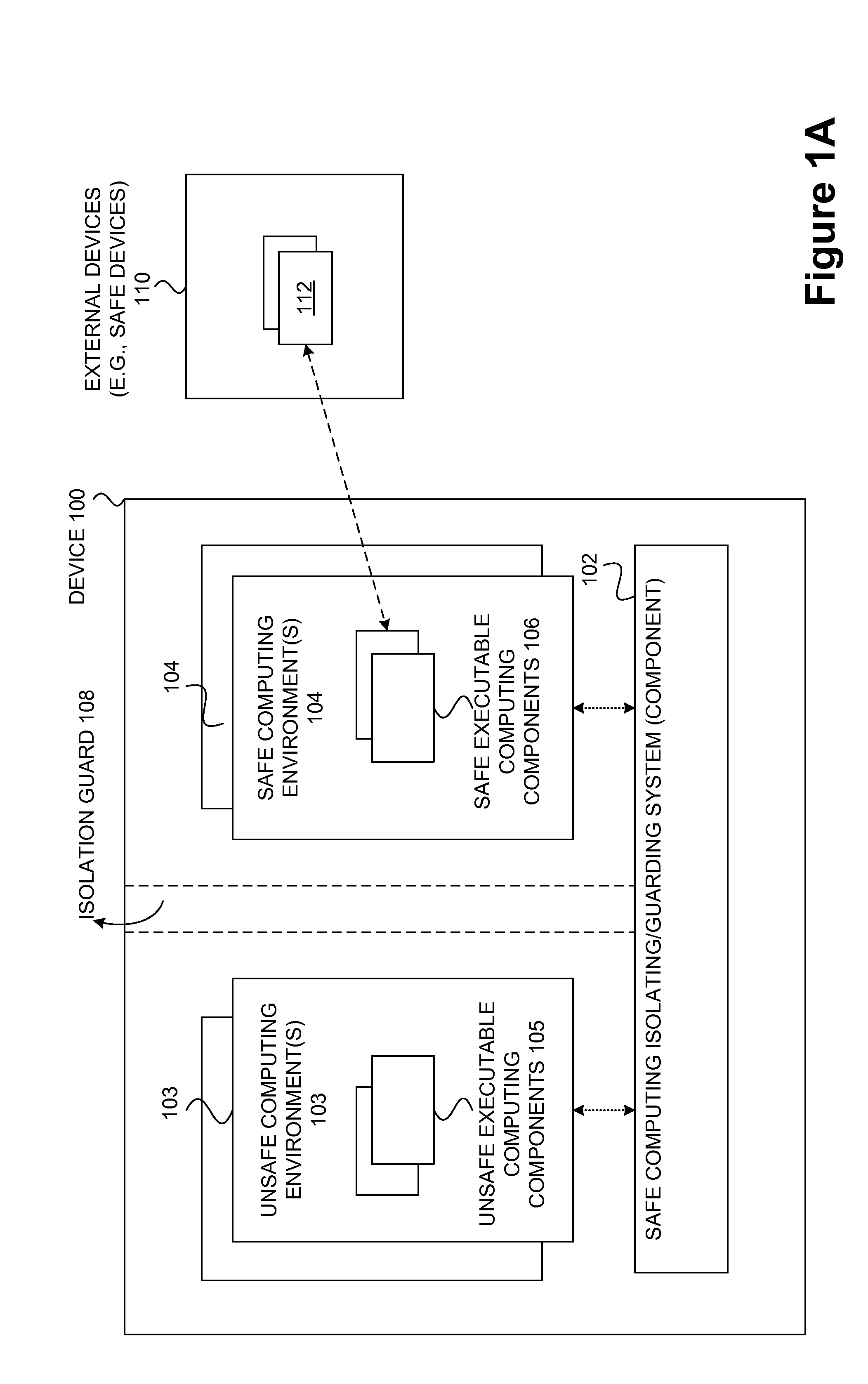
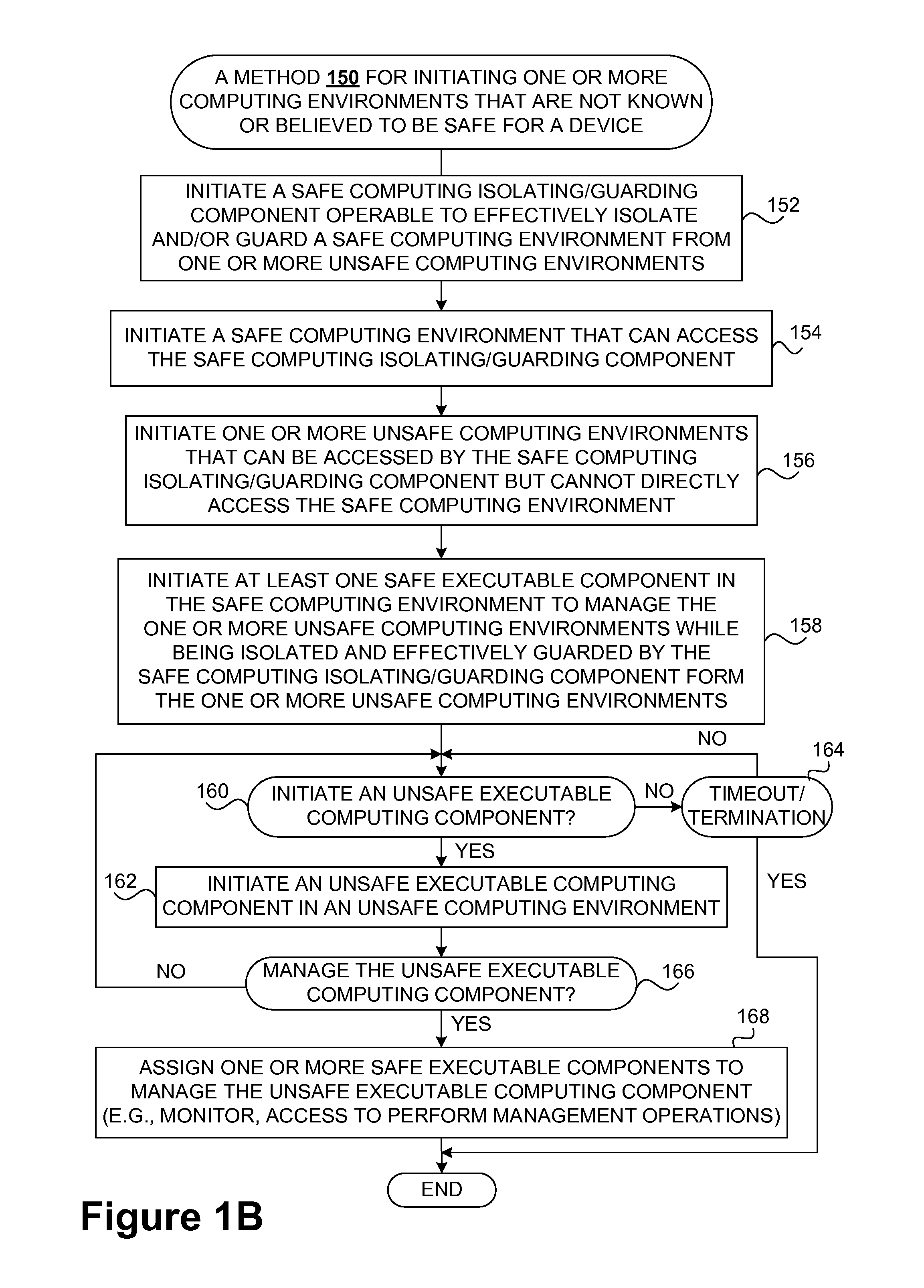
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
Display device and method for manufacturing the same
InactiveUS20060091397A1Improve reliabilityHigh definitionElectroluminescent light sourcesSolid-state devicesSimple Organic CompoundsDisplay device
It is an object of the invention to manufacture a highly reliable display device at a low cost with high yield. A display device of the invention includes: a first reflective electrode layer; and a second transparent electrode layer with an electroluminescent layer interposed therebetween, wherein the electroluminescent layer has a layer containing an organic compound and an inorganic compound, and the first electrode layer contains an aluminum alloy containing at least one or more selected from the group consisting of molybdenum, titanium, and carbon.
Owner:SEMICON ENERGY LAB CO LTD
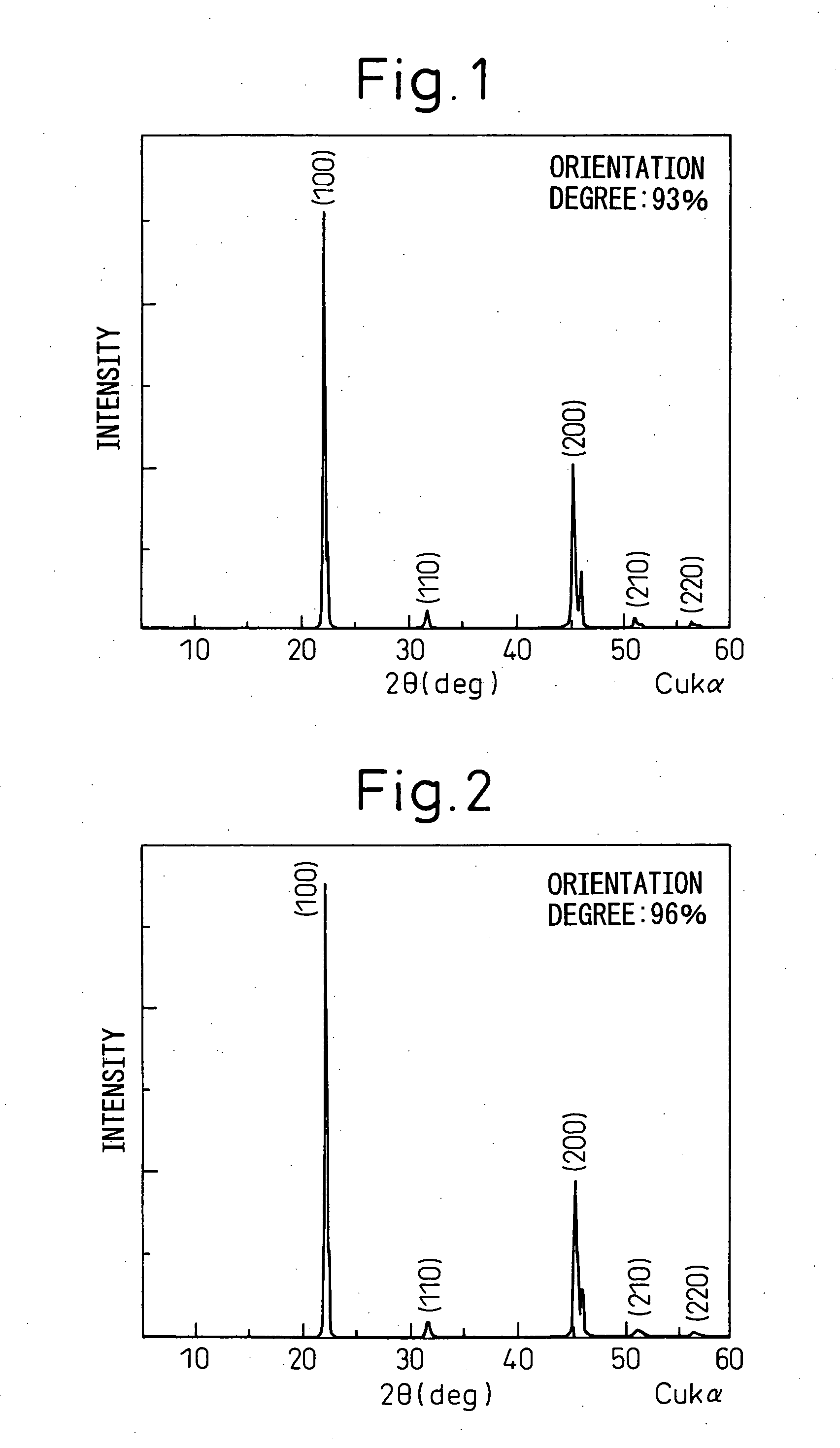
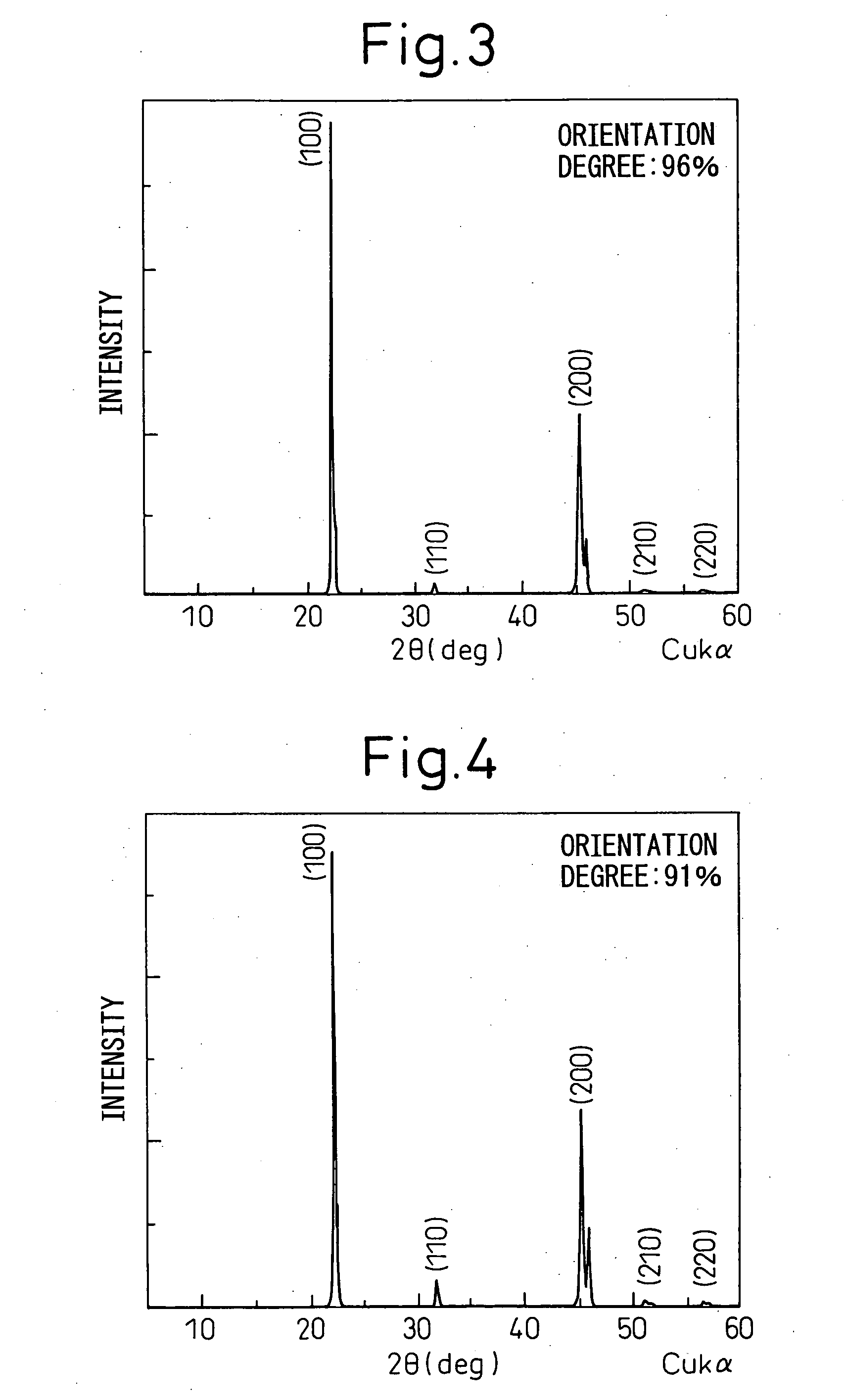
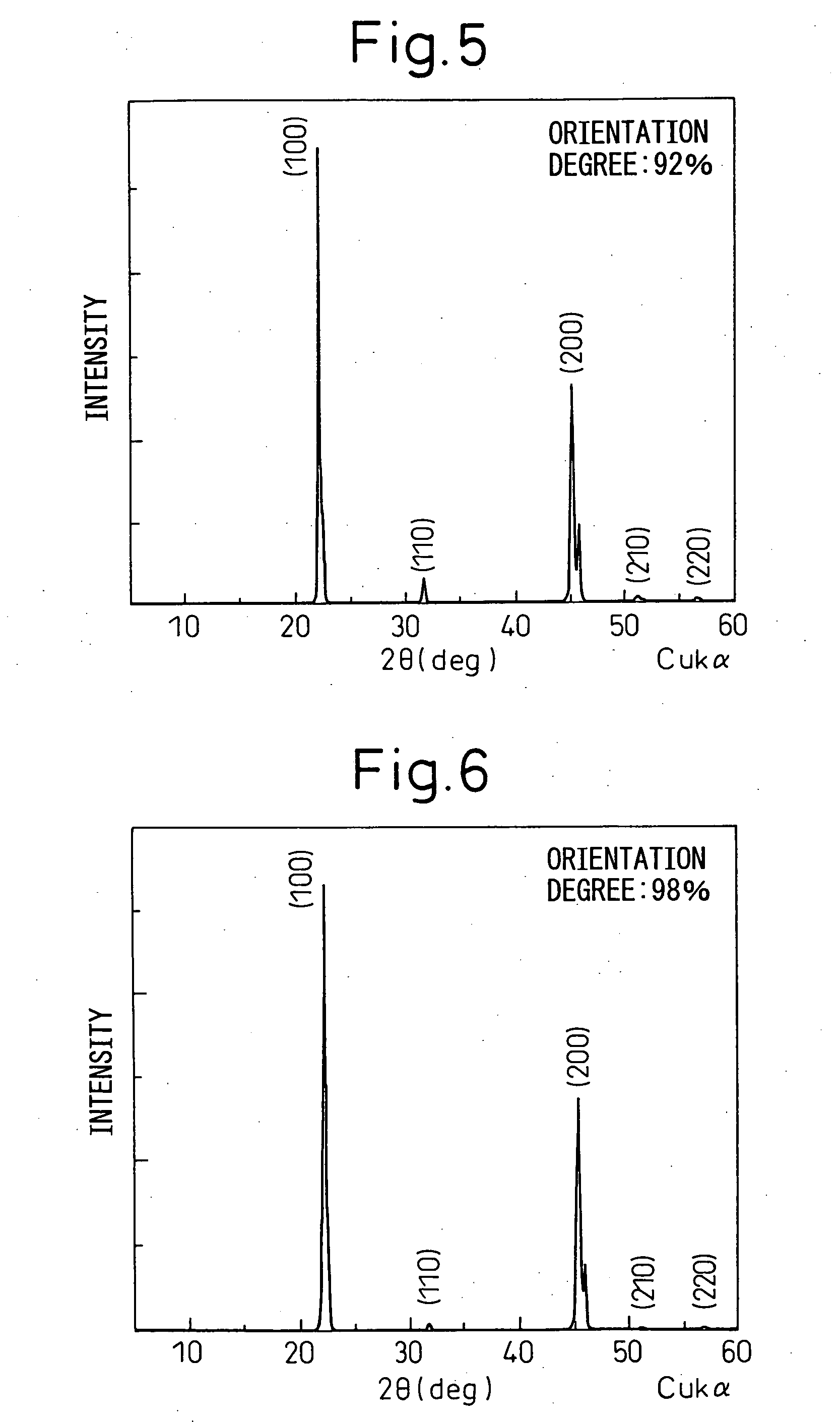
Grain oriented ceramics and production method thereof
InactiveUS20060006360A1Excellent piezoelectric propertiesEnvironment safetyPiezoelectric/electrostrictive device manufacture/assemblyCeramicsAlkaline earth metalCrystal plane
To provide a grain oriented ceramic capable of exerting excellent piezoelectric properties, a production method thereof, and a piezoelectric material, a dielectric material, a thermoelectric conversion element and an ion conducting element each using the grain oriented ceramic, there is provided a grain oriented ceramic comprising, as the main phase, an isotropic perovskite-type compound which is represented by formula (1): {Lix(K1−yNay)1−x}(Nb1−z−wTazSbw)O3 in which x, y, z and w are in respective composition ranges of 0≦x≦0.2, 0≦y≦1, 0≦z≦0.4, 0≦w≦0.2 and x+z+w>0. The main phase comprises a polycrystalline body containing from 0.0001 to 0.15 mol of any one or more additional element selected from metal elements, semimetal elements, transition metal elements, noble metal elements and alkaline earth metal elements belonging to Groups 2 to 15 of the Periodic Table, per mol of the compound represented by formula (1). A specific crystal plane of each crystal grain constituting said polycrystalline body is oriented.
Owner:DENSO CORP
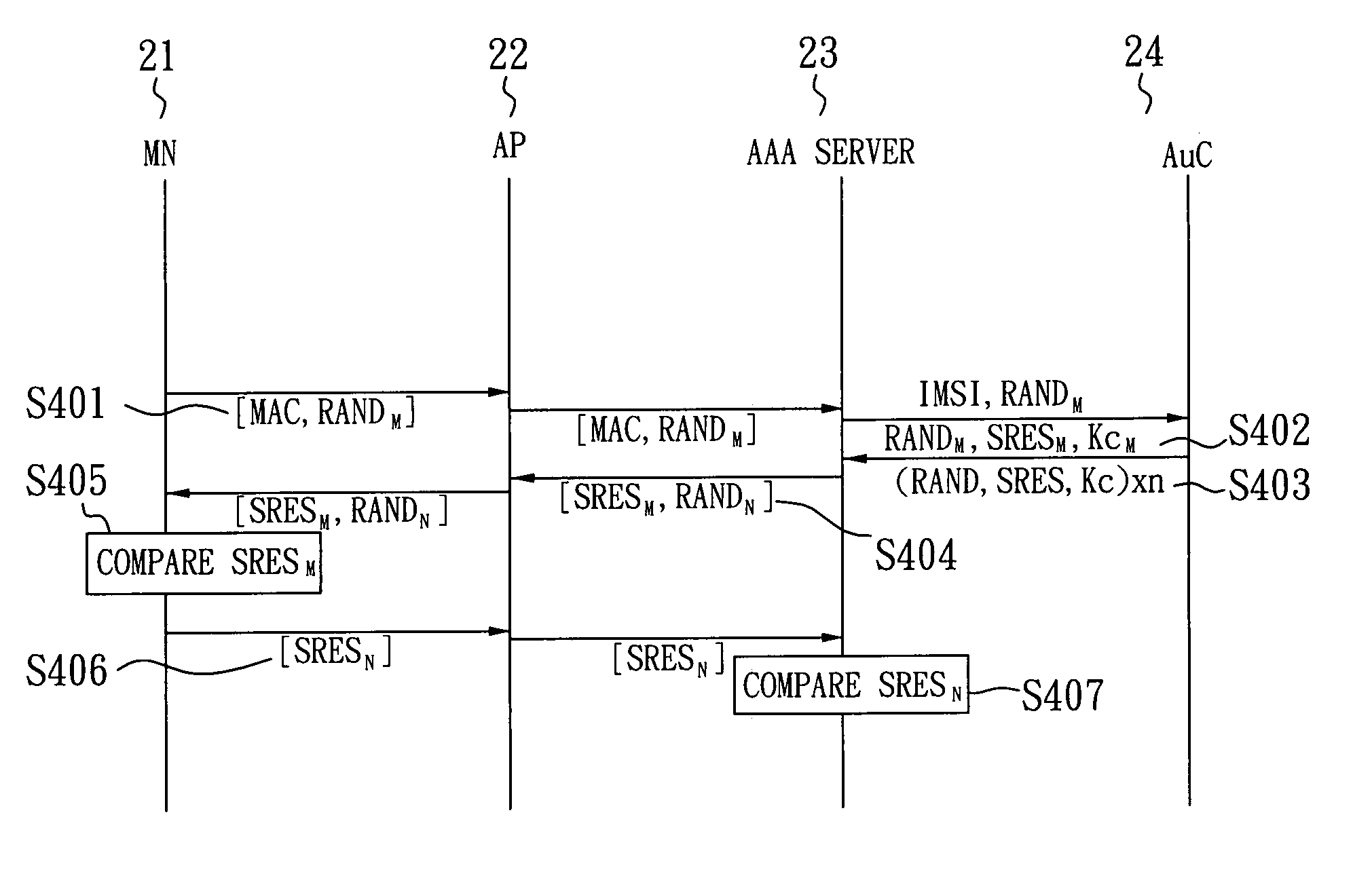
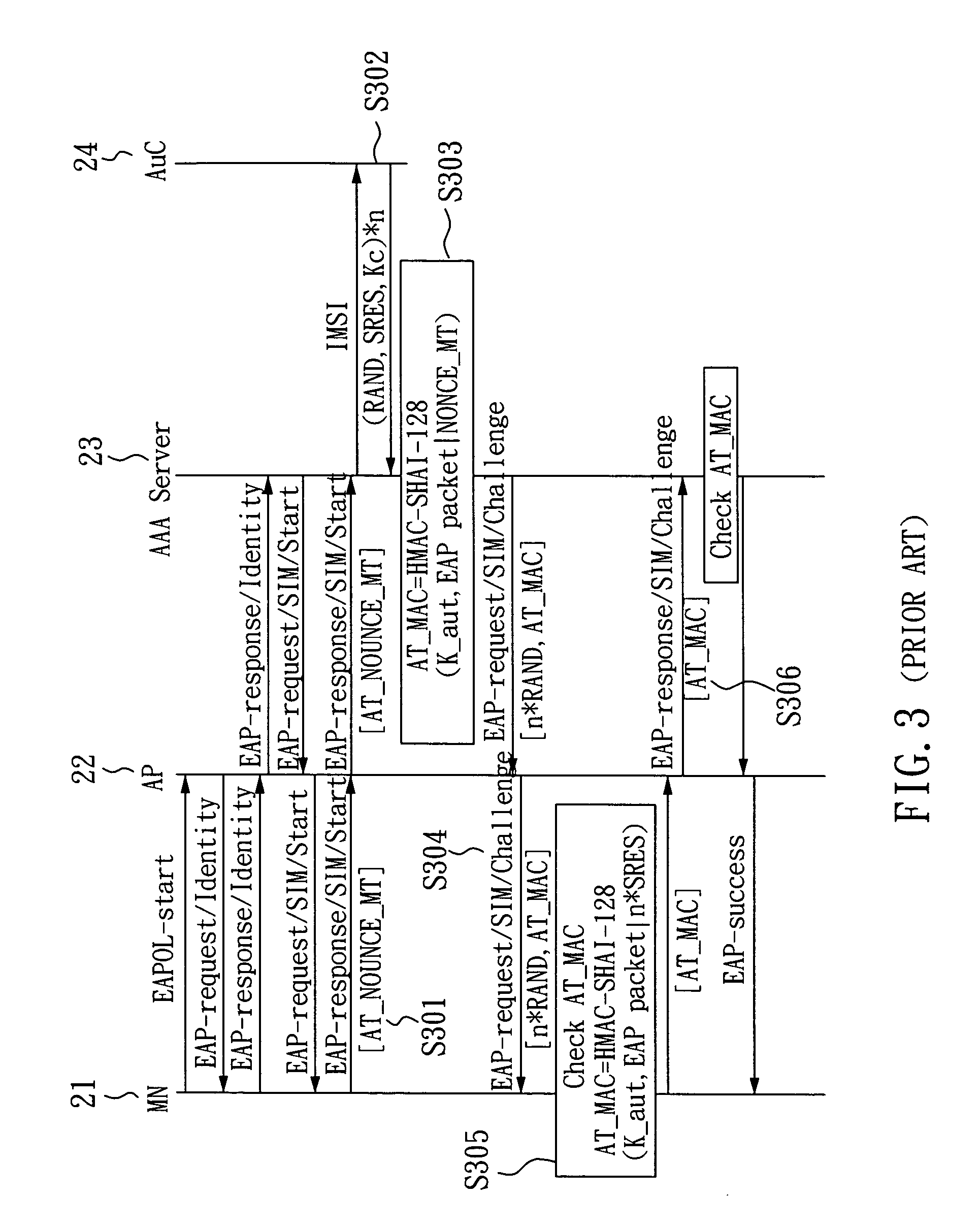
SIM-based authentication method capable of supporting inter-AP fast handover
ActiveUS20050177723A1Blocking in networkSafe WLAN environmentUnauthorised/fraudulent call preventionEavesdropping prevention circuitsFast handoverWireless lan
The invention relates to a SIM-based authentication method capable of supporting inter-AP fast handover, which can decrease the number of authentication procedures without negatively influencing the security of the wireless LAN by establishing an encrypted channel for each mobile node and using method 1: an aggressive key pre-distribution and method 2: probe request triggering passive key pre-query technique, thereby reducing the time of inter-AP handover for the mobile node. Furthermore, a re-authentication procedure is started to update the key after the key is used for a long time so as to ensure that the key is safe, thereby effectively achieving a fast and safe wireless LAN environment.
Owner:IND TECH RES INST
Method and apparatus for improved security in distributed-environment voting
InactiveUS20020129296A1Maintenance safetySatisfy safety performance requirementsRedundant hardware error correctionDistributed computingComputer engineering
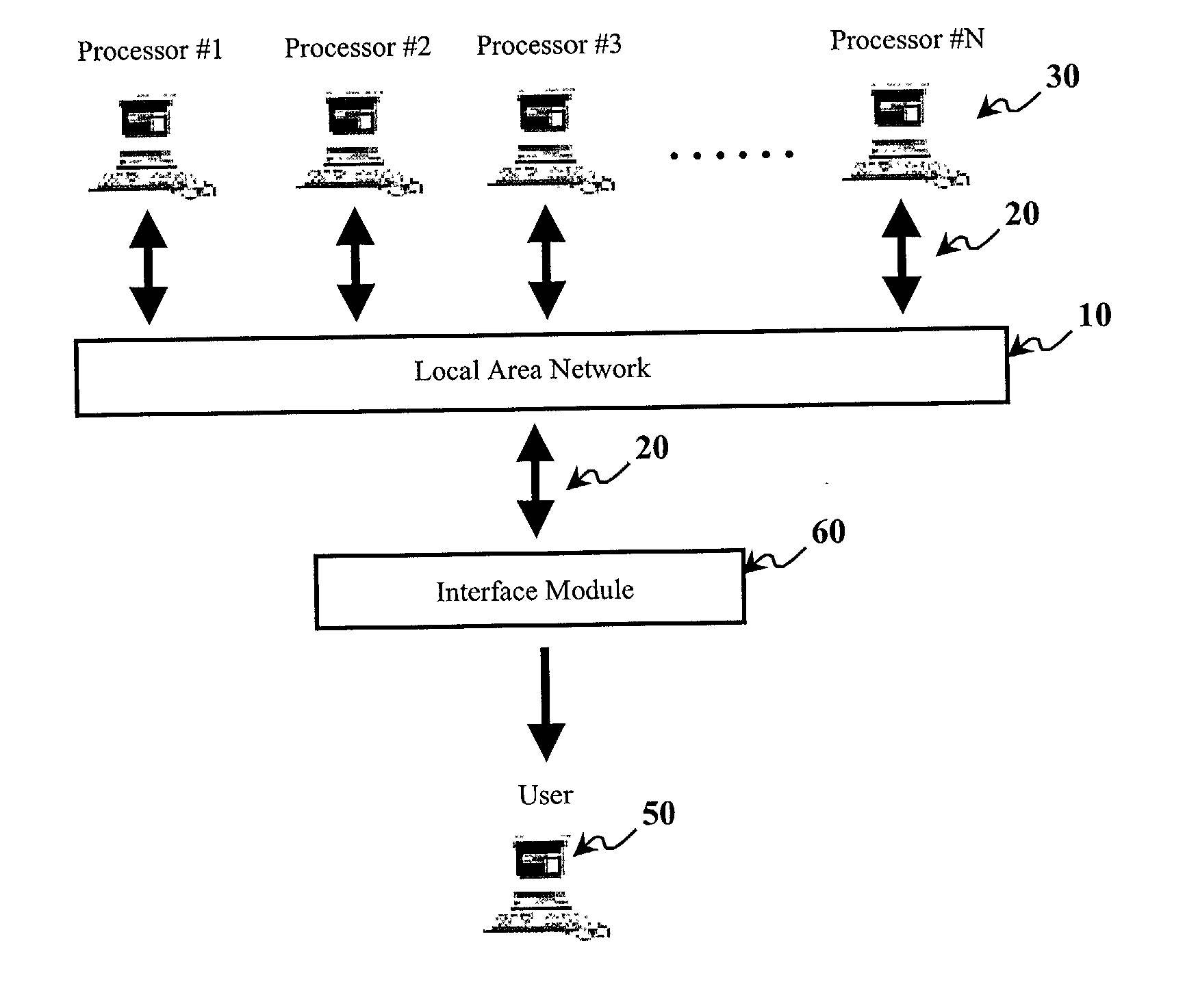
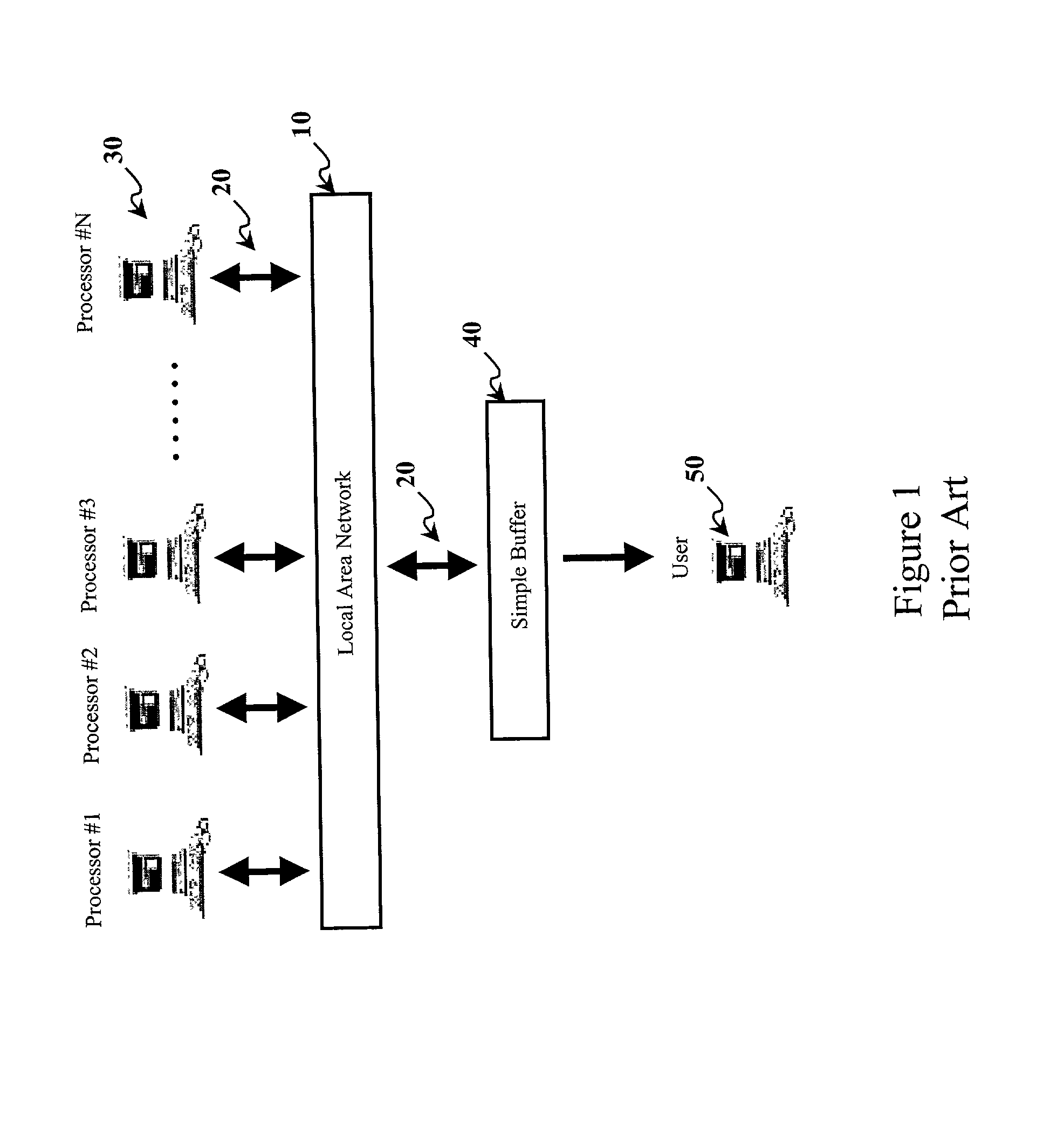
A method and apparatus is disclosed which provides improved security in distributed-environment voting. At least three voting processors running a voting algorithm are connected to a local area network (LAN) and exchange their individually determined results of a process application. Each result is committed to an interface module where it is checked, authenticated and buffered. The allotted time for receiving and buffering committed results is constrained by a first timed interval within the interface module. The first timed interval may be reset several times. The allotted time for checking and comparing the committed results from each processor is constrained by a second timed interval within each voting processor. A majority vote of those authenticated committed results is formed once all necessary iterations of the both the first and second timed intervals are completed. Enhanced security is thereby afforded to the overall voting process and yields a majority vote that is correct despite the introduction of errors associated with faulty or hostile processors.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
Detecting principal directions of unknown environments
ActiveUS20090306881A1Improve autonomous navigationSafely share environmentCharacter and pattern recognitionNavigation instrumentsGraphicsAutonomous Navigation System
Apparatus and methods according to some embodiments of the present invention use a graphical model, such as a Markov random field model, to represent principal driving directions within an environment. The model has a plurality of nodes representing spatial locations within the environment, and the principal direction for each node is determined probabilistically using linear features detected within an image of the environment. Apparatus and methods according to embodiments of the present invention can be used in improved autonomous navigation systems, such as robotic vehicles.
Owner:TOYOTA MOTOR CO LTD
Location, orientation, product and color identification system for the blind or visually impaired
InactiveUS7267281B2Environment safetyNavigational calculation instrumentsTents/canopiesHand heldOutput device
Owner:HOPKINS BILLY D
Youth Based Social Networking
InactiveUS20080281710A1Strengthen restrictionsSafe and secureAdvertisementsDigital data processing detailsSocial webComputer science
The invention provides a method for managing an online social network, the method comprising: establishing criteria for membership in a social network; receiving a request to participate in the social network; obtaining information about the requester; verifying the actual identify of the requester; and determining the eligibility of the requester to participate in the social network based on the established criteria.
Owner:HOAL MARY KAY
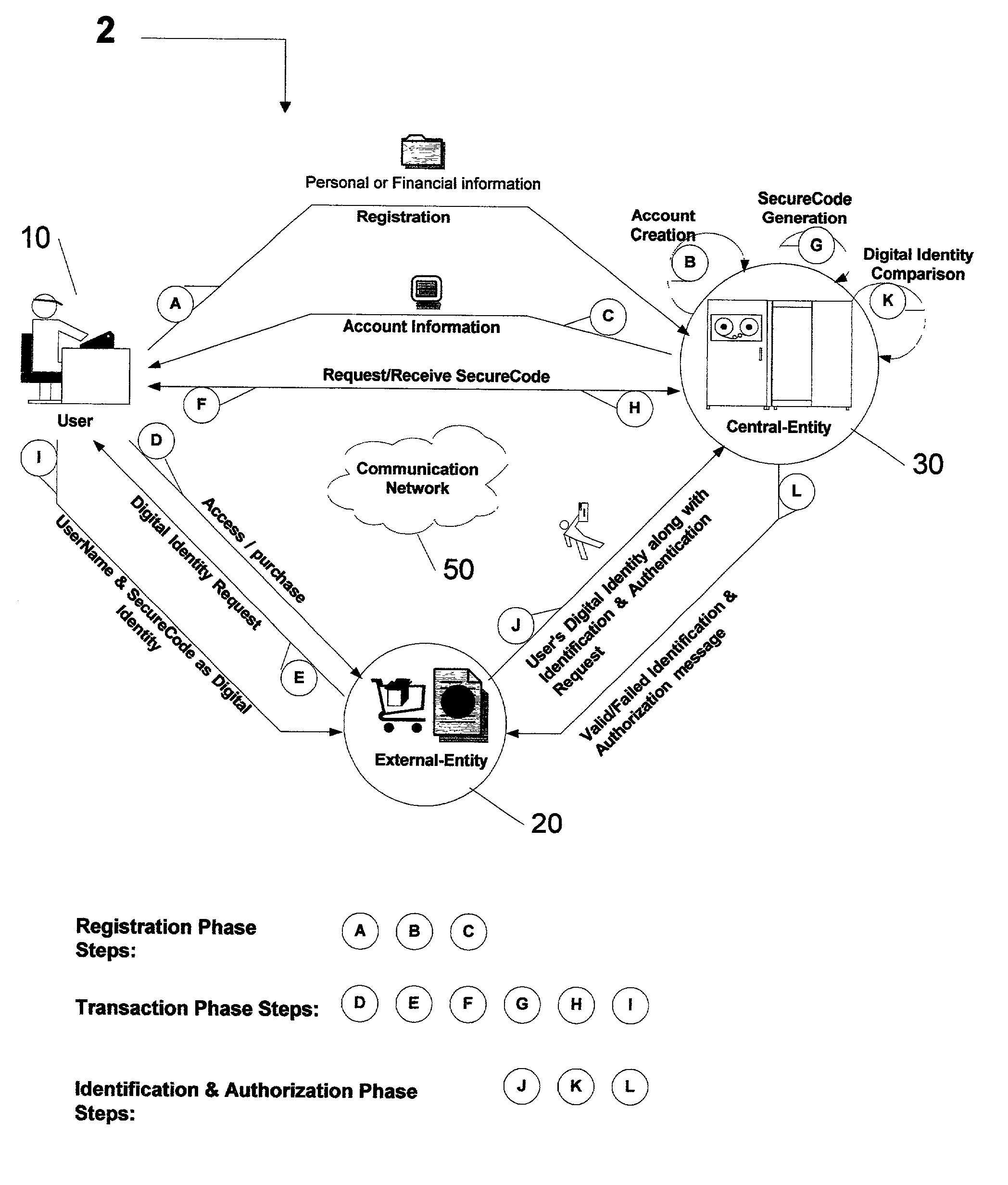
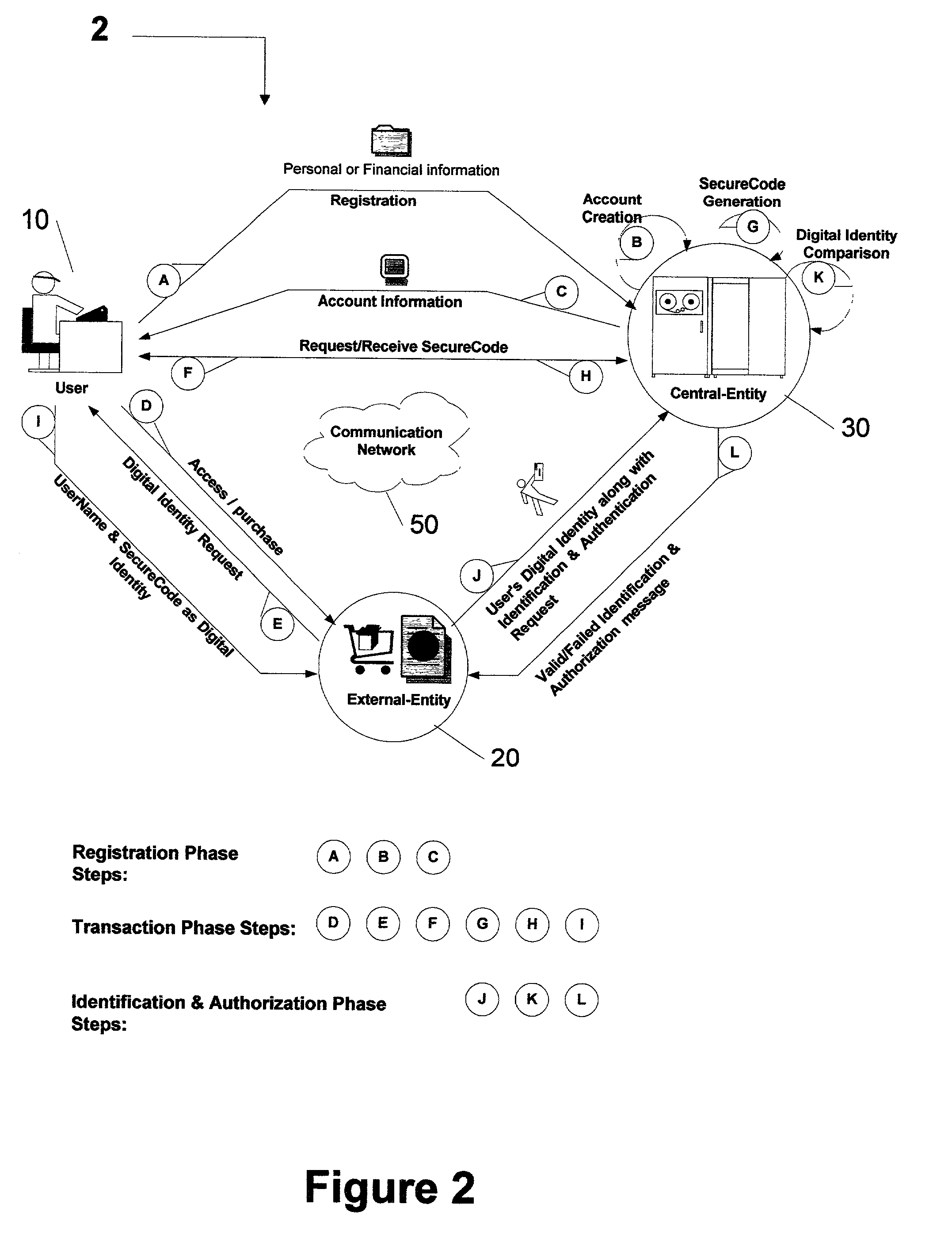
Centralized identification and authentication system and method
ActiveUS7356837B2Reduce fraudImprove securityFinanceDigital data processing detailsDigital identityService provision
A method and system is provided by a Central-Entity, for identification and authorization of users over a communication network such as Internet. Central-Entity centralizes users personal and financial information in a secure environment in order to prevent the distribution of user's information in e-commerce. This information is then used to create digital identity for the users. The digital identity of each user is dynamic, non predictable and time dependable, because it is a combination of user name and a dynamic, non predictable and time dependable secure code that will be provided to the user for his identification.The user will provide his digital identity to an External-Entity such as merchant or service provider. The External-Entity is dependent on Central-Entity to identify the user based on the digital identity given by the user. The External-Entity forwards user's digital identity to the Central-Entity for identification and authentication of the user and the transaction.The identification and authentication system provided by the Central-Entity, determines whether the user is an authorized user by checking whether the digital identity provided by the user to the External-Entity, corresponds to the digital identity being held for the user by the authentication system. If they correspond, then the authentication system identifies the user as an authorized user, and sends an approval identification and authorization message to the External-Entity, otherwise the authentication system will not identify the user as an authorized user and sends a denial identification and authorization message to the External-Entity.
Owner:AMERITECH SOLUTIONS INC
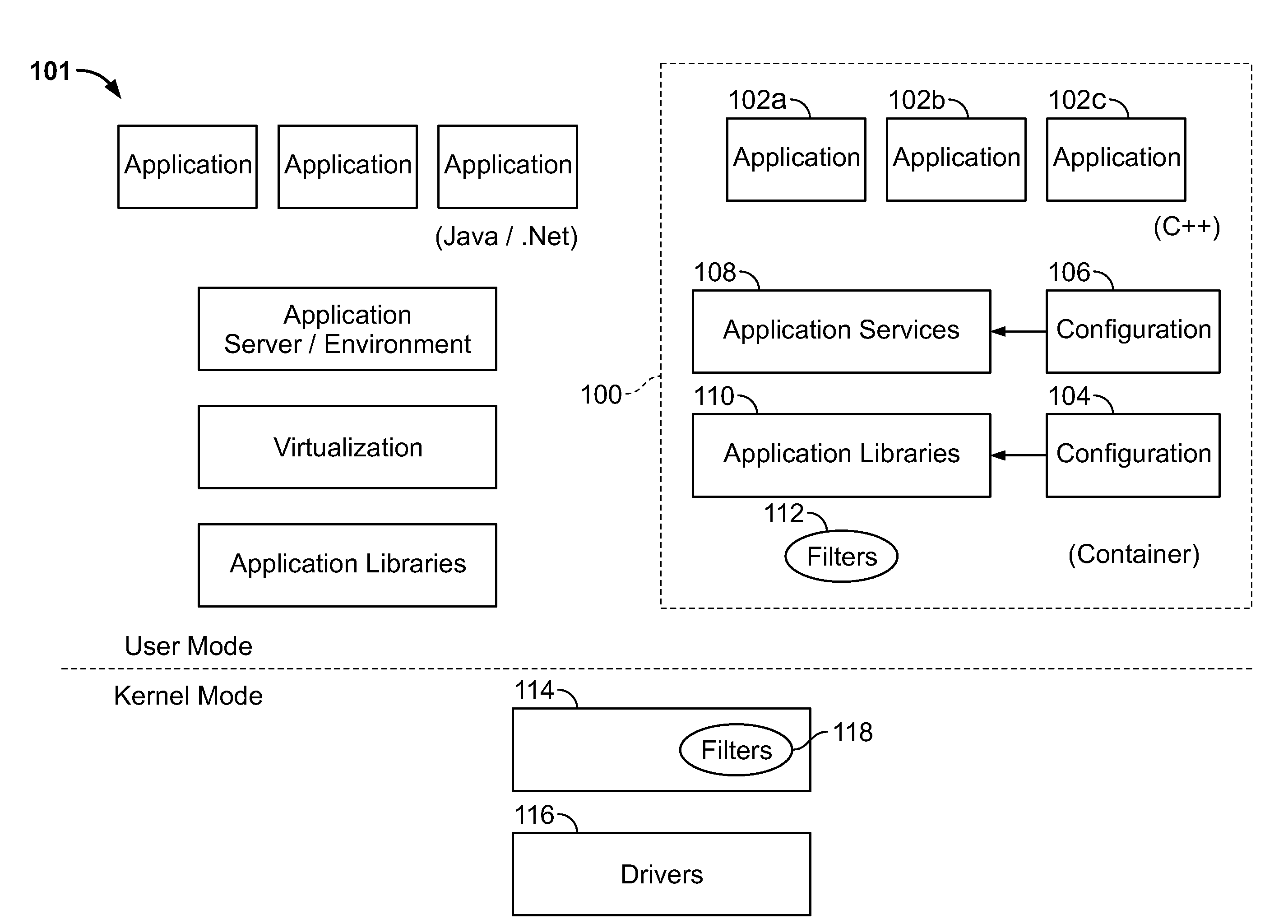
Method and system for providing a program for execution without requiring installation
InactiveUS20080222160A1Environment safetyDigital data processing detailsProgram controlSoftwareLocal kernel
In a method and system for performing a task for a software application that facilitates implementation of the software application with minimized installation requirements, in response to a request by the software application for a local system file of an operating system used for execution of the software application, a processor may redirect the request to access a file stored in a capsule environment together with the software application, where the redirecting includes: updating a table, which a local kernel of the operating system accesses for calling a system call handler, to include a pointer to a filter handler instead of the system call handler, the filter handler, when implemented, passing modified values to the system call handler; and / or causing an application library to redirect a request thereto to a filter library for communicating with the local kernel.
Owner:TRIGENCE CORP
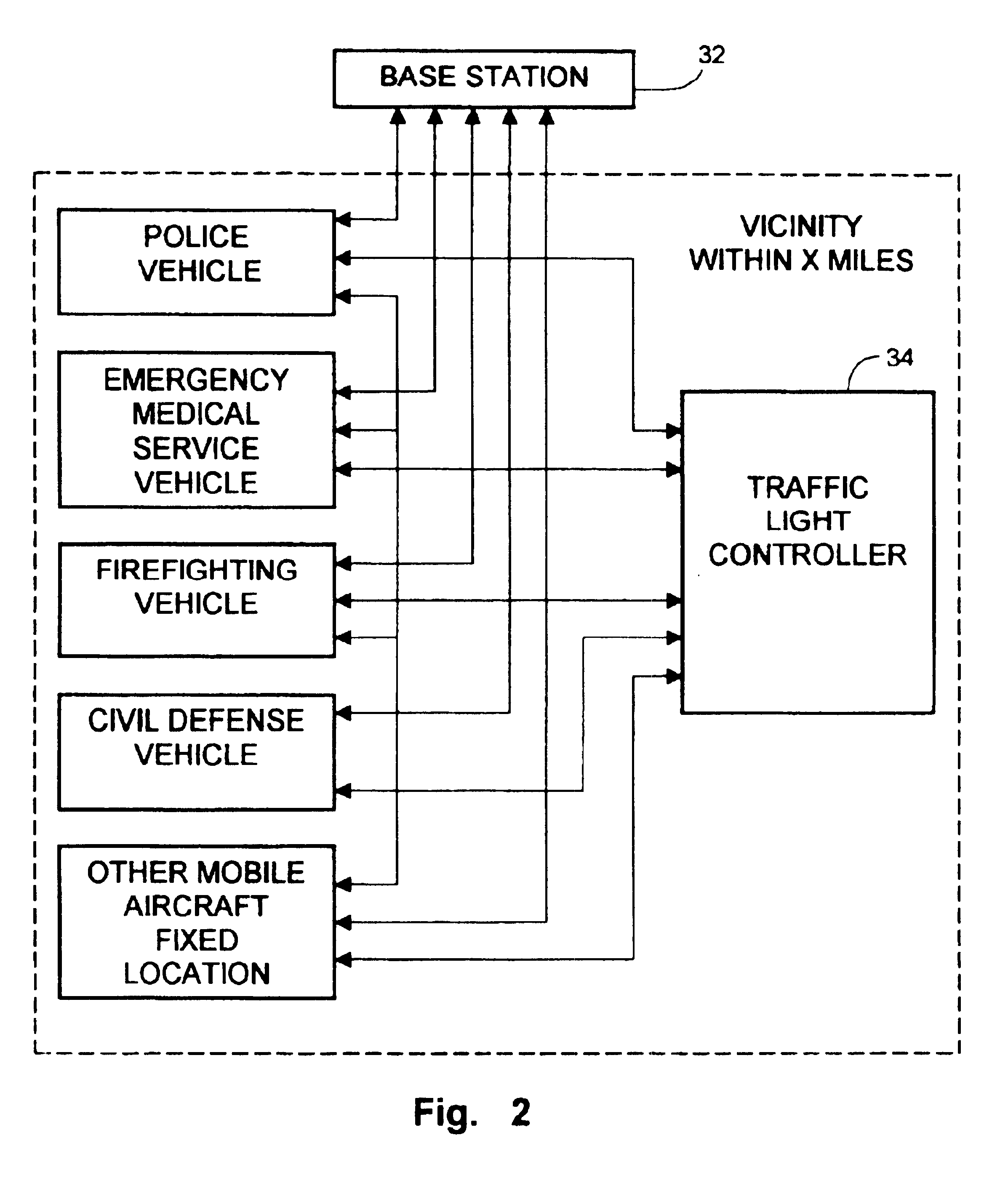
Radio linked vehicle communication system
InactiveUS6917306B2Easy to trackConvenient recordingControlling traffic signalsVehicle testingPersonalizationEngineering
Owner:MCKEOWN SHAWN J
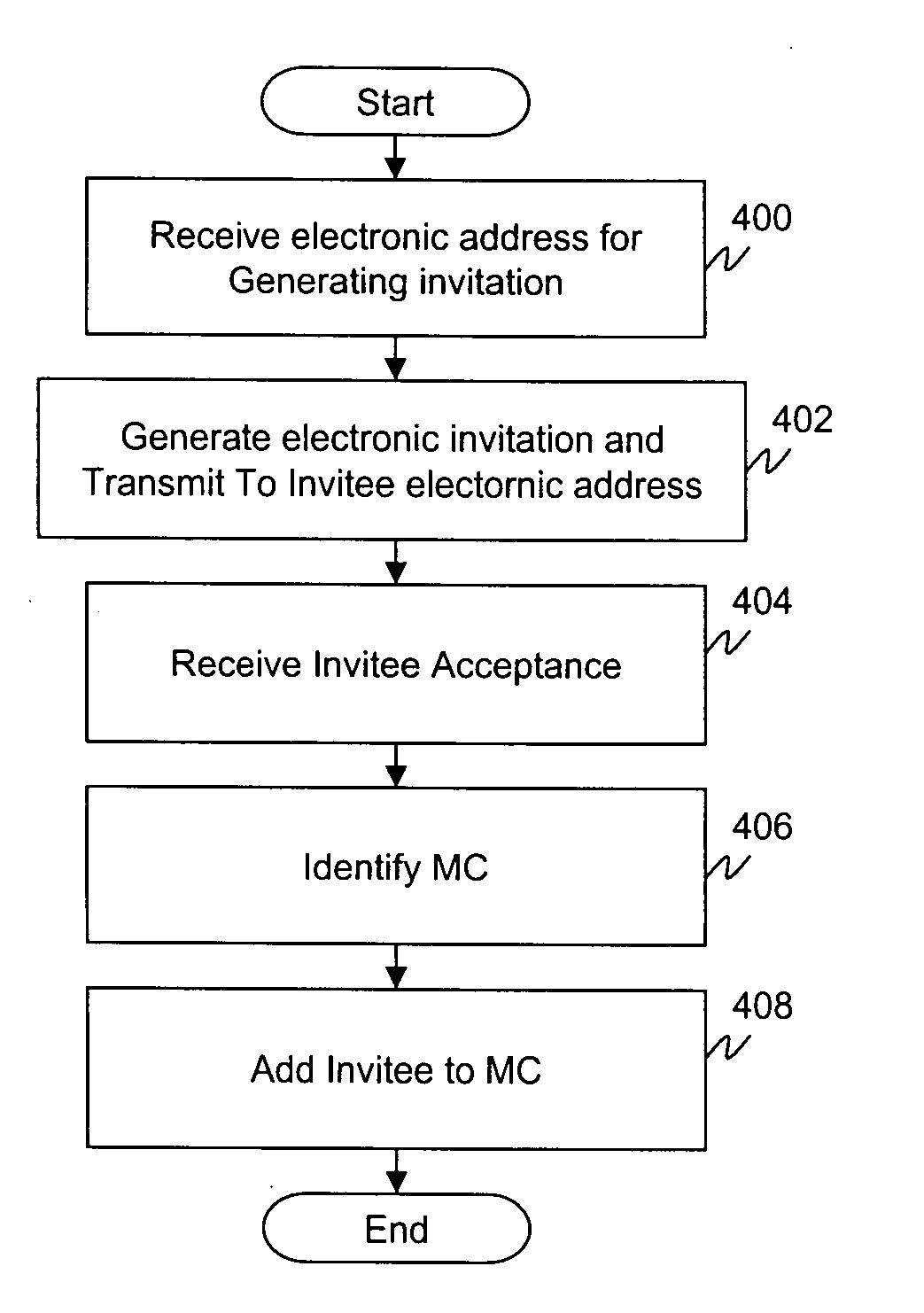
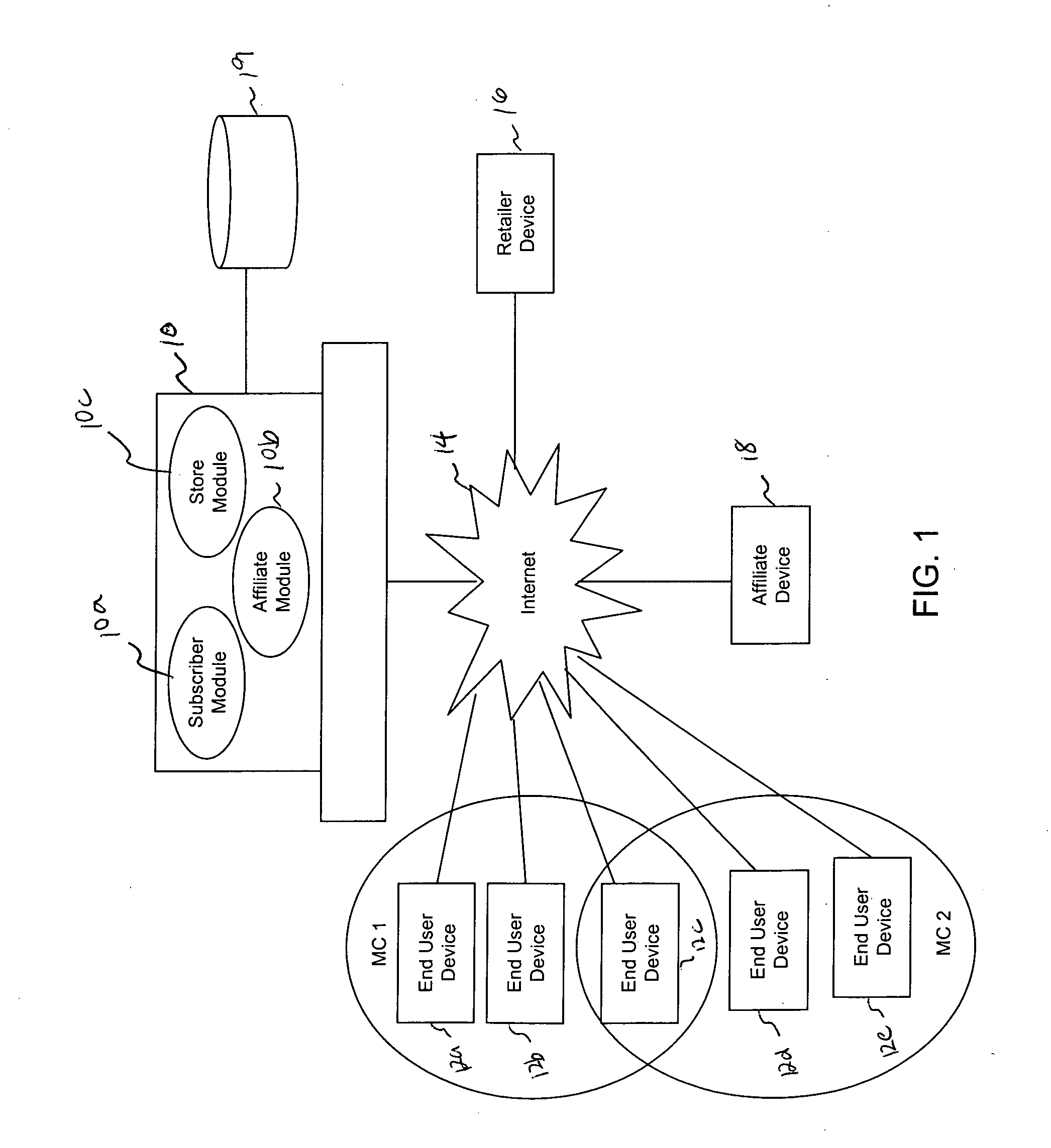
Inferred endorsement system and method
An inferred endorsement (IE) system and method allows members of a micro-community (MC) to share information on experiences with purchased products or services with other members of the MC, via a webpage dedicated to the MC. Once a member of the MC, the member's purchases at participating e-commerce sites may be exposed to the MC by posting it on the webpage. The posting information may be maintained in private so that only the members of the MC may view and comment. The MC creator may populate the MC by inviting potential members to join the MC. An invitee joins the MC upon registering with an IE server hosting the MC webpage. Once a member, the invitee may access the MC webpage and exchange product and service experience information with other MC members.
Owner:REDTOUCAN
Integrated radiation shield
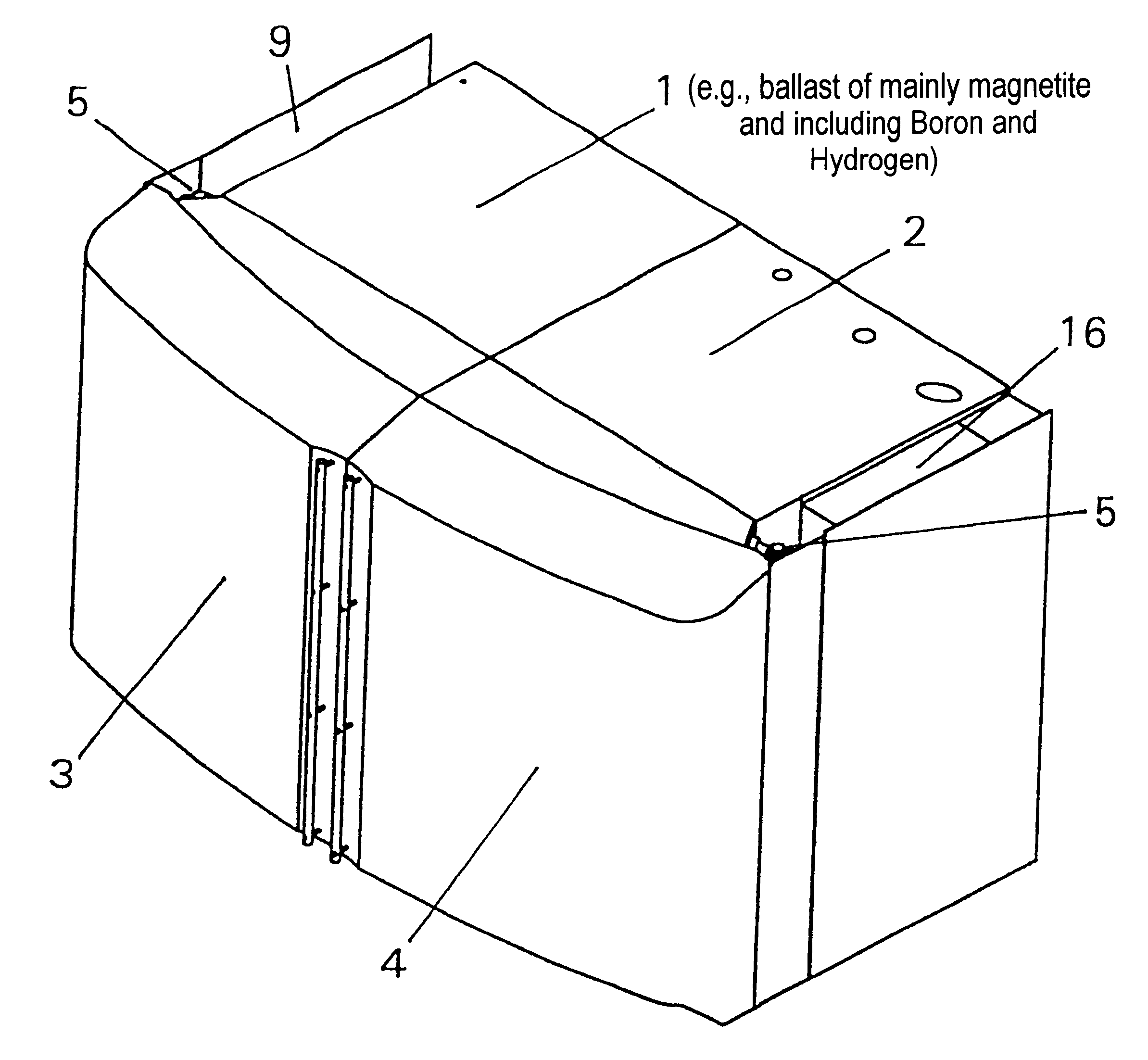
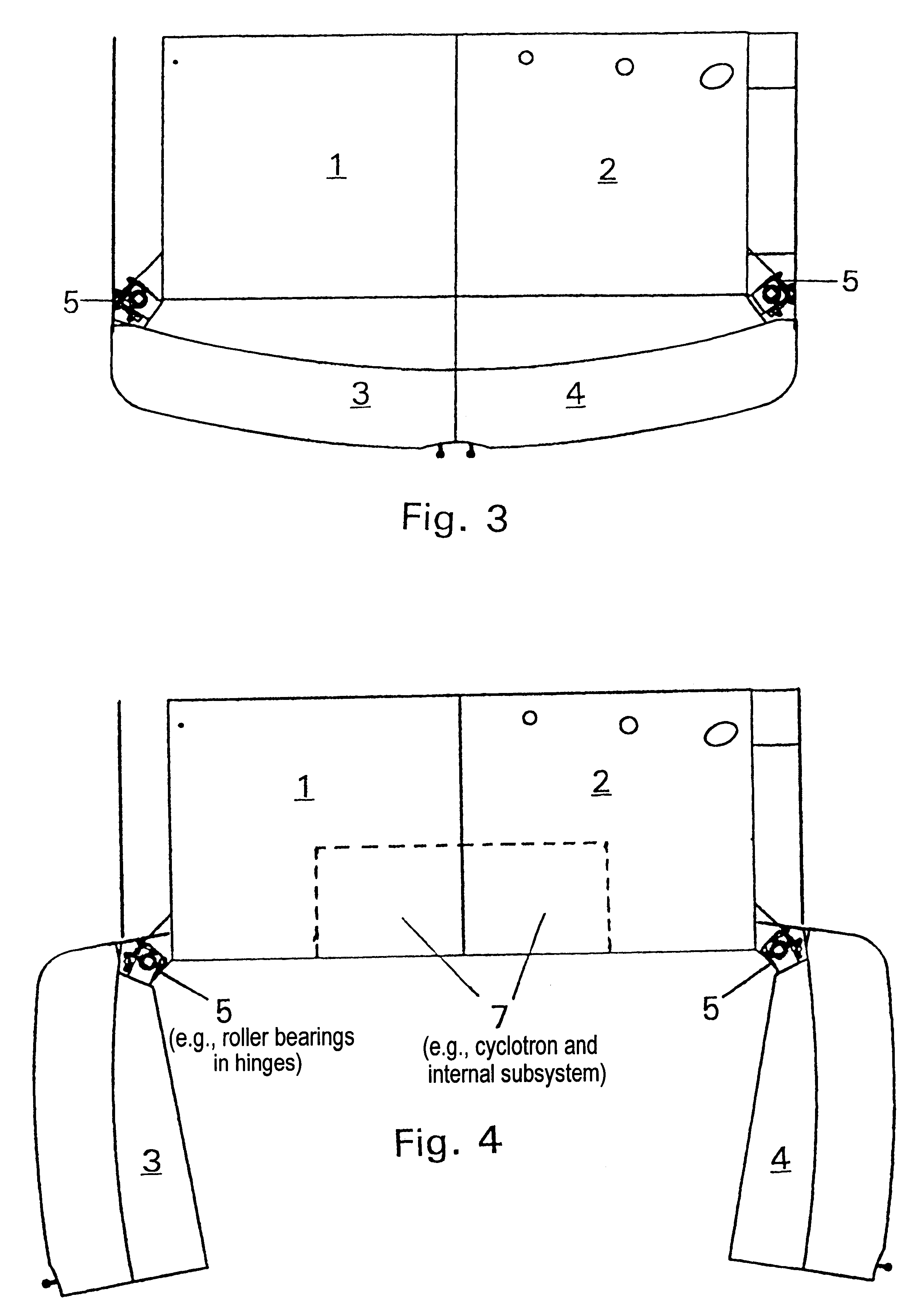
InactiveUS6392246B1Environment safetyEasy to integrateConversion outside reactor/acceleratorsPortable shielded containersEngineeringIsotope
An apparatus is disclosed that forms a basic integrated radiation shield for a PET isotope production system to create a safe environment. The apparatus and the system combine several subsystems to provide a high degree of integration and a nice aesthetic impression. The apparatus contains a cyclotron system and contains integrated target media handling for gas targets and water dispensing systems for water targets. A compartment including first and second additional radiation shields, respectively, that contains additional processing systems. The apparatus forms a closed radiation-proof system by means of a casing formed of four molded sections. A first and second section constitute a main body containing;the cyclotron system and a third and a fourth section constituting a pair of tight doors for encompassing the cyclotron into a sealed radiation shield. The first section additionally contains a Waste Gas Delay Line embedded in its shielding material.
Owner:GEMS PET SYST
Blocks and building system for the construction of lifesize inflatable play structures
A system for the construction of life size play structures includes a multiplicity of inflatable building blocks, each being a member of a finite set of different multi-sided block types. Each such type is a cylinder having the cross section of a regular polyhedron, and the length of each side of each polyhedron is identical. The blocks are attached to each other by means of a rotating joint which aligns each contiguous side of each block with the contiguous side of the adjoining block, but which does not allow each such to translate relative to the adjoining block. The joints are constructed at fixed locations along the sides according to specific dimensional ratios. Stiffening means are used to maintain the dimensional integrity of each block, and to maintain the uniformity of the system from block to block.
Owner:LIOU DICK
CRM Security Core
A security core supports a networked banking app for a client application device communicating with a server, such as e.g. a smartphone. It provides a secure environment for the banking app to conduct registration, enrollment, and transaction workflows with corresponding back-end servers on the network. It includes defenses against static analysis, attempts at reverse engineering, and real-time transaction fraud. A principal defense employed is obfuscation of the protocols, APIs, algorithms, and program code. It actively detects, thwarts, misdirects, and reports reverse engineering attempts and malware activity it senses. A routing obfuscator is configured to operate at the outer layer. Previous core designs are retained as camouflage. An internal TLS library is used rather than the OS TLS layer. Cookies are managed internally in the core rather than in the webkit-browser layer.
Owner:CRYPTOMATHIC LTD
Process and a plant for recycling carbon dioxide emissions from power plants into useful carbonated species
ActiveUS7596952B2Useful carbonated speciesEnvironment safetyCalcium/strontium/barium carbonatesGas turbine plantsAtmospheric airNegative carbon dioxide emission
A process is disclosed for recycling carbon dioxide emissions from a fossil-fuel power plant into useful carbonated species The process primarily comprises the steps of: a) burning the fossil fuel, thereby generating heat and a hot exhaust gas containing CO2; and b) converting the heat into energy. The process is characterized in that it further comprises the steps of: c) cooling the exhaust gas; and d) biologically transforming the CO2 contained in the cooled exhaust gas into carbonated species, thereby obtaining a low CO2 exhaust gas and producing useful carbonated species. The low CO2 exhaust gas obtained in step d) can be released in the atmosphere without increasing the problem of greenhouse effect.
Owner:SAIPEM SPA
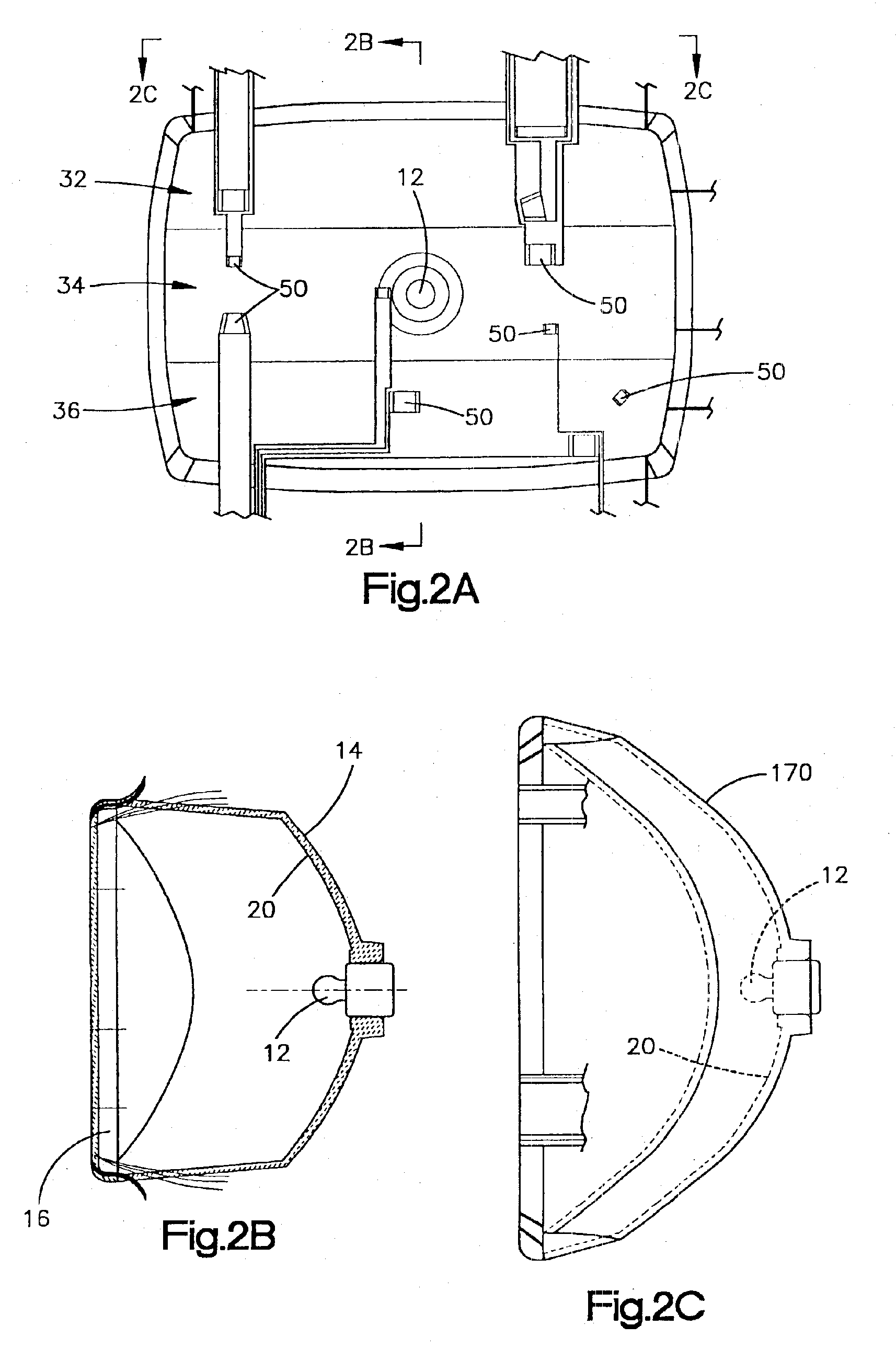
Lamp masking method and apparatus
InactiveUS6913375B2Environment safetyDirect controlVehicle headlampsLighting support devicesElectricityOptoelectronics
A motor vehicle lamp assembly having a light source for emitting light and a source enclosure having a light transmissive portion for transmitting light from the light source to an illumination zone. The enclosure is affixed with a material which covers a selected region of the light transmissive portion of the enclosure. The material is electrically energized to alter an amount of light transmitted from the light source to the illumination zone. A drive circuit electrically coupled to the material energizes the material to control a light output from the lamp assembly.
Owner:ILLUME
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com